
USB port locker for pc keygen,serial,crack,generator
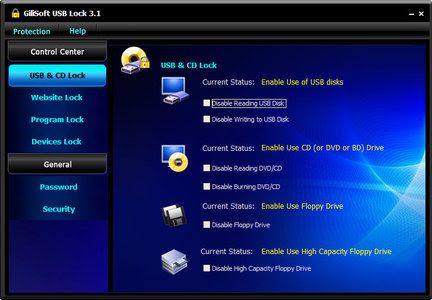
USB port locker for pc keygen,serial,crack,generator
GETTING STARTED: Hardware Key and Licenses []
Hardware Key and Licenses
E-Prime is a copy-protected system requiring a hardware key that connects to the computer’s USB port. The hardware key copy protection scheme limits the number of development machines to the number of licenses purchased. The hardware key is required for registration of E-Prime Other applications require the hardware key to be installed depending on the type of license in use.
&#;
NOTE:&#;Users should not experience any problems installing or using E-Prime if the hardware key is correctly in place and the serial number was correctly entered. However, if the hardware key should fail, contact PST Product Service and Support immediately via cromwellpsi.com
&#;
Single User License
A Single User License allows the user to develop experiments on one computer at a time. The hardware key must be connected during registration of E-Prime , and while developing experiments within E-Studio. E-Studio will not load if the hardware key is not connected. With the Single User License, users may install E-Prime on multiple machines, and simply move the hardware key to the machine to be used for experiment development. If more than one concurrent development station is necessary, additional Single User License must be purchased.
Runtime License
The Runtime application (E-Run) is not copy protected. E-Run may be installed on up to 25 machines within a single lab, and used for data collection on multiple machines simultaneously with a Runtime Only installation.
&#;
Network License
A Network License permits the development of E-Prime experiments on multiple machines used concurrently within the licensed department, up to the number of purchased seats. The Network License requires the hardware key to be connected to a network machine and the network connection to be active during the registration and validation process, and while developing experiments within E-Studio.
&#;
See Also:
GETTING STARTED: Installation, Registration, Validation, and Updates []
5 best software to block USB ports
USBDeview
USBDeview is also a free tool and one of the top USB block software programs that deserve your attention. Made by NirSoft, it allows you to enable and disable USB port lock.
With the help of this freeware, you will be able to view the list of USB ports and also the devices that are connected to them.
Here are its highlights:
- This program lists all USB devices that are currently connected to your system and the USB devices that were previously used.
- For each of the USB devices, you will see displayed extended information including the following: device’s name and description, type, serial number, the date and time that it was added to your system, VendorID, ProductID and more.
- In order to enable and disable USB ports, you will have to select a port from the list of ports and then click on the Red button to disable it or the Green button to enable it.
- You can also uninstall USB devices that you have previously used and disconnect the USB devices that are currently connected to your system.
- You will get the chance to use the USBDeview program on a remote computer as long as you log in to that system with admin user.
⇒ Download USBDeview
Conclusion
These were our 5 top USB block software solutions. With their help, you can prevent unauthorized access to your PC and stop malware spreading to your PC through the USB ports.
After you take a look at their extended sets of features, you’ll definitely be able to make an informed decision that will provide enhanced safety for your system.
Even so, we recommend you to check out the best antivirus solutions for USB flash drives so that you can maximize security.
If you have any other suggestions or questions, drop them in the comments section below and we&#;ll surely take a look.
FAQ: Learn more about USB port blockers
- How to block access to USB ports?
You can disable USB ports from Device Manager, but a safer solution is to use one of the USB port blockers from this list, especially if you&#;re a novice.
- What to do if USB port is not working?
If your USB port isn&#;t working, check out our quick-fix article to reinstall drivers, make registry modifications, install updates, and more.
- How to fix USB not recognized in Windows 10?
If Windows 10 doesn&#;t recognize USB, you can turn off Fast Startup, update your drivers, partition your USB storage, and more.
Editor’s Note: This post was originally published in September and has been since revamped and updated in May for freshness, accuracy, and comprehensiveness.
Software protection dongle
A software protection dongle (commonly known as a dongle or key) is an electronic copy protection and content protection device. When connected to a computer or other electronics, they unlock software functionality or decode content.[1] The hardware key is programmed with a product key or other cryptographic protection mechanism and functions via an electrical connector to an external bus of the computer or appliance.[2]
In software protection, dongles are two-interface security tokens with transient data flow with a pull communication that reads security data from the dongle. In the absence of these dongles, certain software may run only in a restricted mode, or not at all. Apart from software protection, dongles can enable functions in electronic devices, such as receiving and processing encoded video streams on television sets.
History[edit]
The Merriam-Webster dictionary states that the "First known use of dongle" was in and that the etymology was "perhaps alteration of dangle."[3]
Dongles rapidly evolved into active devices that contained a serial transceiver (UART) and even a microprocessor to handle transactions with the host. Later versions adopted the USB interface, which became the preferred choice over the serial or parallel interface.
A advertisement for Rainbow Technologies claimed the word dongle was derived from the name "Don Gall". Though untrue, this has given rise to an urban myth.[4]
Usage[edit]
Efforts to introduce dongle copy-protection in the mainstream software market have met stiff resistance from users. Such copy-protection is more typically used with very expensive packages and vertical market software such as CAD/CAM software, cellphone flasher/JTAG debugger software, MICROS Systems hospitality and special retail software, Digital Audio Workstation applications, and some translation memory packages.
In cases such as prepress and printing software, the dongle is encoded with a specific, per-user license key, which enables particular features in the target application. This is a form of tightly controlled licensing, which allows the vendor to engage in vendor lock-in and charge more than it would otherwise for the product. An example is the way Kodak licenses Prinergy to customers: When a computer-to-plate output device is sold to a customer, Prinergy's own license cost is provided separately to the customer, and the base price contains little more than the required licenses to output work to the device.
USB dongles are also a big part of Steinberg's audio production and editing systems, such as Cubase, WaveLab, Hypersonic, HALion, and others. The dongle used by Steinberg's products is also known as a Steinberg Key. The Steinberg Key can be purchased separately from its counterpart applications and generally comes bundled with the "Syncrosoft License Control Center" application, which is cross-platform compatible with both Mac OS X and Windows.
Some software developers use traditional USB flash drives as software license dongles that contain hardware serial numbers in conjunction with the stored device ID strings, which are generally not easily changed by an end-user. A developer can also use the dongle to store user settings or even a complete "portable" version of the application. Not all flash drives are suitable for this use, as not all manufacturers install unique serial numbers into their devices.
Although such medium security may deter a casual hacker, the lack of a processor core in the dongle to authenticate data, perform encryption/decryption, and execute inaccessible binary code makes such a passive dongle inappropriate for all but the lowest-priced software. A simpler and even less secure option is to use unpartitioned or unallocated storage in the dongle to store license data. Common USB flash drives are relatively inexpensive compared to dedicated security dongle devices, but reading and storing data in a flash drive are easy to intercept, alter, and bypass.
Issues[edit]
There are potential weaknesses in the implementation of the protocol between the dongle and the copy-controlled software. It requires considerable cunning to make this hard to crack. For example, a simple implementation might define a function to check for the dongle's presence, returning "true" or "false" accordingly, but the dongle requirement can be easily circumvented by modifying the software to always answer "true".
Modern dongles include built-in strong encryption and use fabrication techniques designed to thwart reverse engineering. Typical dongles also now contain non-volatile memory &#; essential parts of the software may actually be stored and executed on the dongle. Thus dongles have become secure cryptoprocessors that execute program instructions that may be input to the cryptoprocessor only in encrypted form. The original secure cryptoprocessor was designed for copy protection of personal computer software (see US Patent 4,,, Sept 18, )[5] to provide more security than dongles could then provide. See also bus encryption.
Hardware cloning, where the dongle is emulated by a device driver, is also a threat to traditional dongles. To thwart this, some dongle vendors adopted smart card product, which is widely used in extremely rigid security requirement environments such as military and banking, in their dongle products.
A more innovative modern dongle is designed with a code porting process which transfers encrypted parts of the software vendor's program code or license enforcement into a secure hardware environment (such as in a smart card OS, mentioned above). An ISV can port thousands of lines of important computer program code into the dongle.[citation needed]
In addition, dongles have been criticized because as they are hardware, they are easily lost and prone to damage, potentially increasing operational costs such as device cost and delivery cost.
Game consoles[edit]
Some unlicensed titles for game consoles (such as Super 3D Noah's Ark or Little Red Hood) used dongles to connect to officially licensed ROM cartridges, in order to circumvent the authentication chip embedded in the console.[citation needed]
Some cheat code devices, such as the GameShark and Action Replay use a dongle. Typically it attaches to the memory card slot of the system, with the disc based software refusing to work if the dongle is not detected. The dongle is also used for holding settings and storage of new codes, added either by the user or through official updates, because the disc, being read only, cannot store them. Some dongles will also double as normal memory cards.
See also[edit]
References[edit]
External links[edit]
What’s New in the USB port locker for pc keygen,serial,crack,generator?
Screen Shot
System Requirements for USB port locker for pc keygen,serial,crack,generator
- First, download the USB port locker for pc keygen,serial,crack,generator
-
You can download its setup from given links:


