
602 Messaging Server v3.32c serial key or number

602 Messaging Server v3.32c serial key or number
IMPORTANT! READ BEFORE UPGRADE or INSTALL
If you are on Windows 7, please make sure the following updates are NOT installed. If they are installed, please uninstall them first or you may experience issues with upgrade!:
- KB
- KB
- KB
* Detail information and uninstall instruction can be viewed from following Technical Bulletin: Windows OS Updates Preventing DW Spectrum Upgrade
If the OS is Ubuntu or lower version, OS must be upgraded to or higher prior to upgrade or install DW Spectrum Refer to the Reference section of the for the related Knowledgebase article.
DW Spectrum Release Note for
CRITICAL COMPATIBILITY NOTICE:
All users must update to the v or higher Mobile release in order to be able to connect to a v System via the Mobile Client. Mobile Clients v or earlier will not be able to access Systems running v or later.
BREAKING CHANGES
Mac OS X , , support is dropped: Desktop Client will not work on these OS versions.
NEW FEATURES:
o Push Notifications (requires Mobile Client v or later):
§ Rules can be created in DW Spectrum to send Push Notifications to mobile devices.
§ Users can receive push notifications from multiple systems and turn on/off notifications for specific systems.
§ In order to receive Push Notifications, users must be logged into the Cloud in Mobile Client.
§ Users can create custom text for notifications in the Rules Engine via Desktop Client.
o Health Monitoring - Available in the Server Web Admin interface and Cloud Portal, Health Monitoring provides administrators detailed information about a System’s health, including, but not limited to:
§ Alerts - automatically detected / identified problems with a System
§ System Info (# of servers, channels, storage located, users, and version)
§ Servers (storage detailed state, CPU usage, NICs state, hardware spec, etc.)
§ Cameras (online/offline state, resolution, fps, quality, firmware version, etc.)
§ Storage Locations (path, server, type, status, read/write rate, size, usage %)
§ Network Interfaces (name, server, state, IP address, I/O rates)
§ Desktop Clients connected to Servers.
o New Embedded Browser - Desktop Client now uses a full-featured embedded Chromium browser (v) to display web pages on layouts:
§ Download Files on Web-Page - the embedded browser in Desktop Client now supports downloading and saving files.
§ Cameras Web Page in Camera Settings Dialog - camera web pages can now be opened up in the Camera Settings dialog allowing users to configure/access camera web pages inside Desktop Client even when on a different Subnet (i.e., remote connections / outside the LAN / WAN). Server acts like an HTTP(s) proxy from cameras to Desktop Clients.
o Video Wall Failover - If a Server with Video Wall licenses fails, the video wall continues working for 7 days. After that, it will be blocked with the error message "Not enough licenses".
IMPROVEMENTS
o Best Server Selection (while connecting to a Cloud-connected Multi-Server System):
§ In prior releases, Desktop Client would connect to a random available server via Cloud. Now Cloud connections are routed through the Server with the best uplink.
§ Added the ability for users to specify the preferred Server for connections. The configured Desktop Client will attempt to connect to the preferred Server first, and if it is not reachable, it will detect and connect via the Server with the best uplink.
o 2-way Audio API - Allows third-party web clients to send audio (from client microphone) to and get audio from cameras.
o Added Time Zone option for Virtual Cameras - Time Zone can now be specified for virtual cameras. If "Time Zone" is set to "Auto", then the time zone is defined by metadata or UTC if there's no time zone specified in the file. If set to "Client", the Time Zone is defined by the desktop client.
o Server Side Motion Detection improved - False positives detection introduced to increase accuracy of detected motion events (e.g., turning on/off lights or switching camera day/night mode are now likely to be ignored)
o Additional action parameter placeholders for the "Do HTTP request" action - Placeholders can be added to the HTTP POST request body to be automatically replaced by the corresponding values from Analytics Event parameters. This feature is only applicable to Analytics and Generic Events. Placeholders syntax:
§ {cromwellpsi.comId} – replaced by the camera ID (e.g., {{{ad1d1b6cfd4-ffe}}})
§ {cromwellpsi.comName} – replaced by the camera name (e.g., DWC-MB45WiAT)
§ {cromwellpsi.comype} – replaced by the event type (e.g., cromwellpsi.comInTheArea or cromwellpsi.comossing)
§ {cromwellpsi.comame} – replaced by the event name (e.g., Object in the area or Line crossing)
§ {cromwellpsi.comn} – replaced by the caption (e.g., “Line crossing - impulse event (caption)”)
§ {cromwellpsi.comption} – replaced by the description (e.g., "Line crossing - impulse event (description)").
o Improved MacOS performance and introduced an experimental setting to limit frame rate and reduce CPU load (see Local Settings -> Advanced).
o Improved cloud connectivity on certain network environments.
o Added the ability to pin the Timeline in fullscreen mode:
§ When the Timeline is pinned it will remain fixed on the screen.
§ If the Timeline is pinned in fullscreen mode and the user leaves fullscreen it will be pinned for all cameras on the layout when the user returns to fullscreen mode.
o Database backups are now categorized into the following types:
§ Created after system merge
§ Created after updates
§ Initiated via API
§ Scheduled.
o "Camera selection" dialog was optimized for a large systems.
o Added text search in the "Event log" dialog.
o "Global Notification Settings" button was removed from the "Show Notification" action.
o Added .mpegts files to the list of supported files in Desktop Client.
o It is now possible to disable port 80 on firewalls completely and use port for HTTPS connection.
o Added the ability to search by object types in the Notification Panel. <param>: <value> returns object where <param> has <value>. For instance, if there are analytic plugins that recognize t-shirt color, gender, and glasses, it is possible to search for analytic events by “T-Shirt: White”, “Gender: Male”, “Glasses: True”.
o The default playback state of a camera opened from the Notification Panel has changed. Now a camera remains on Pause once opened.
o Users are now imported from LDAP with their Email addresses.
o It is now possible to open multiple instances of the Desktop Client by double clicking on the desktop shortcut.
o Added information about remaining license deactivations on "License details" and "Confirmation" dialog.
NEW DEVICE SUPPORT
o New Devices Supported with Analog Encoder License:
§ Digital Watchdog DW-EN4K16
o New PTZ camera support
§ DWC-MPTZXW, DWC-MPTZXW
RECOMMENDED UPGRADE PATH
- From 3.x: Upgrade directly to DW Spectrum
- From or Upgrade to then upgrade to
* Always backup the database and license key information before upgrading to newer build or version
** Re-index the storage after upgrading to
IN_CLIENT UPGRADE INFORMATION
- Build Number:
- Password:1uis6p
INSTALLATION FILE DOWNLOAD
cromwellpsi.com
OS SUPPORTED – MEDIASERVER
- Windows 7, 8, , 10 Pro/Enterprise
- Windows Server R2, , R2, v and later,
- Ubuntu LTS: , ,
- OPERATING SYSTEM NO LONGER SUPPORTED
- 32 Bit operating system (both Windows and Ubuntu Linux)
- Ubuntu is no longer supported.(refer to the reference for upgrade
- Windows Server no longer supported (Only R2 is supported)
OS SUPPORTED – CLIENT
- Windows: 7 Home, 7 Standard, 7 Pro, 7 Ultimate, 8/ Standard, 8/ Pro, Enterprise, 10 Home/Pro/Enterprise1
- Windows Server R2, , R2, v
- Ubuntu LTS: , ,
- MAC OS X “Mojave”, “Catalina”.
1 For Windows 10, recommend i5/i7 processors with 16GB RAM and video card with 4GB or higher RAM
- OPERATING SYSTEM NO LONGER SUPPORTED
- 32 Bit operating system (both Windows and Ubuntu Linux)
- Ubuntu is no longer supported.(refer to the reference for upgrade instruction)
- Windows Server no longer supported (Only R2 is supported)
- MAC OSX , , support is dropped. Desktop client will not work on these OS versions.
MOBILE APP
- DW Mobile Plus
- DW Spectrum™ App x.x
- DW Site Viewer™ App for Apple TV
SUPPORTED BLACKJACK AND CAAS MODELS
USB2 - Device including authentication glyph - Google Patents
This application claims priority to and is a non-provisional of U.S. provisional patent application No. 61/,, filed on Nov. 13, , which is herein incorporated by reference in its entirety for all purposes.
There are a number of ways to authenticate individuals. One method normally used for identifying a user is based on a secret identification code, also referred to as a PIN (Personal Identification Number). In a typical transaction involving a payment card, a user enters his PIN into a transaction terminal, which then communicates with a back end server computer. The back end server computer thereafter verifies that the PIN code is accurate. Although PINs are useful, there are some disadvantages. For example, the owner of the card must memorize the PIN and another person can commit fraud by stealing the PIN.
Another way to authenticate individuals is to use biometrics such as fingerprint readers. Although biometrics can be useful, there are disadvantages. For example, biometric devices are expensive to implement. Further, biometric data can be stolen. For example, fingerprints of individuals can be left on glasses and other objects. Such fingerprints could be replicated by others by creating fake fingerprint impressions. Like a PIN, once biometric data is stolen, it is possible for an unauthorized person to use this data to impersonate a real user.
Static signatures may also be used to authenticate a person. However, a static signature can be forged or electronically intercepted by unauthorized persons.
Embodiments of the invention address these and other problems, individually and collectively.
Systems and methods for improved methods and devices are disclosed.
One embodiment of the invention is directed to a device comprising a processor, a display coupled to the processor, and a computer readable medium coupled to the processor. The computer readable medium comprises (i) code for displaying a first authentication image comprising a plurality of image elements comprising a set of image elements, where the image elements in the set of image elements are located at a first set of positions on a display screen, (ii) code for receiving a first glyph having a first configuration corresponding to the set of image elements from a user while the first authentication image is displayed, (iii) code for displaying a second authentication image comprising the plurality of image elements comprising the set of image elements, where the image elements in the set of image elements are located at a second set of positions on the display screen, where the second set of positions is different than the first set of positions, and (iv) code for receiving a second glyph having a second configuration corresponding to the set of image elements from a user while the second authentication image is displayed.
Another embodiment of the invention is directed to a method comprising displaying a first authentication image comprising a plurality of image elements comprising a set of image elements. The image elements in the set of image elements are located at a first set of positions on a display screen. The method also includes receiving a first glyph having a first configuration corresponding to the set of image elements from a user while the first authentication image is displayed, and displaying a second authentication image comprising the plurality of image elements comprising the set of image elements. The image elements in the set of image elements are located at a second set of positions on the display screen. The second set of positions is different than the first set of positions. The method further includes receiving a second glyph having a second configuration corresponding to the set of image elements from a user while the second authentication image is displayed.
Another embodiment of the invention is directed to a method comprising displaying a first image element and receiving a glyph. The glyph is created by moving the first image element from a first position relative to a second image element to a second position relative to the second image element. The method also includes sending an authentication message comprising data representing the glyph to a service provider.
Another embodiment of the invention is directed to a device comprising a processor, a display coupled to the processor, and a computer readable medium coupled to the processor. The computer readable medium comprises code for displaying a first image element, receiving a glyph, where the glyph is created by moving the first image element from a first position relative to a second image element to a second position relative to the second image element, and code for sending an authentication message comprising data representing the glyph to a service provider.
Further details regarding embodiments of the invention are provided below in the Detailed Description with reference to the Figures.
One embodiment of the invention is directed to a method for authenticating a user (e.g., a consumer) in a transaction such as a payment transaction. Although payment transactions are discussed in detail, it is understood that embodiments of the invention can be used in other transactions such as money transfer transactions or access transactions (e.g., obtaining access to a particular location or venue).
The method comprises, in a first transaction, displaying a first authentication image comprising a plurality of image elements comprising a set of image elements on a display screen on a device such as a personal computer, a mobile phone, or an access device. The display screen can comprise a touch screen. A touch screen can allow a user to input data into the device by contacting the screen with a finger or a stylus. The image elements in the set of image elements are located at a first set of positions on the display screen.
Any suitable type or number of image element can be displayed on the display screen. Suitable image elements may comprise images of two or three dimensional objects, or parts thereof. Examples of two dimensional objects might be simple shapes such as squares or circles, or streets or landmarks on a two-dimensional map. Examples of three-dimensional objects may include pictures of buildings, mountains, rocks, etc.
After the first authentication image is displayed, a first glyph having a first configuration corresponding to the set of image elements is received by the device while the first authentication image is displayed on the display screen. A user may use his finger or a stylus to create a glyph that corresponds to the set of image elements.
As used herein, a “glyph” can be a figure that can be drawn on the display screen using a finger, stylus, cursor, or the like. A mouse or other input device can be used to create a glyph. The glyph and/or the stroke(s) used to form the glyph may be continuous or discontinuous in nature, and they can be simple or complex. An example of a continuous figure can be in the shape of a letter such as the letter “Z,” “C,” “S,” or some other complex or simple shape. An example of discontinuous strokes used in a glyph can be a glyph in the form of the letter “X”.
Illustratively, a) shows a phone comprising a display screen coupled to a housing . The display screen shows a first authentication image comprising first plurality of image elements in the form of an array of differently patterned or colored dots (a)-(i). The user may enter a first glyph into the phone using his finger to sequentially connect dots (a), (d), (g), and (h) to form the first glyph . The dots (a), (d), (g), and (h) can form a set of image elements. The first glyph may or may not be displayed on the display screen . If it is not displayed on the display screen , then the first glyph would still be received by the phone .
After the first glyph is received by the device, the device can have an authentication module (e.g., authentication software) which authenticates the user by comparing the first glyph to a previously registered glyph. In other embodiments, the device may send data representing the entered glyph to a remote server computer. The remote server may have an authentication module (e.g., authentication software) which authenticates the user by comparing the first glyph to a previously registered glyph. In either case, if the first glyph matches a previously registered glyph (which may be stored in a database accessible to the remoter server or which may be stored in the device itself), then the user is authenticated and the user may then be allowed to proceed with the transaction. Conversely, if the first glyph does not match the previously registered glyph, then the user is not authenticated and the user may not be allowed to proceed with the transaction. Alternatively, additional authentication steps may be required before the user can proceed with the transaction. For example, a service provider may request that the user call the service provider and provide additional information (e.g., the user's mother's maiden name) before the transaction can proceed.
At some point in time, the user may then subsequently conduct a second transaction using the device (or a different device). The user may initiate a second transaction. The same or different device that was used to conduct the first transaction may then display a second authentication image. The second authentication image may comprise the plurality of image elements comprising the set of image elements.
In the second authentication image, however, the image elements in the set of image elements are located at a second set of positions on the display screen. The second set of positions is different than the first set of positions.
A second glyph having a second configuration corresponding to the set of image elements is received from a user while the second authentication image is displayed. Because the positions of the image elements that are displayed during the second transaction are different than the positions of the image elements that are displayed during the first transaction, and because the second glyph will correspond to the same set of image elements, the first and second glyphs will have different configurations.
Referring to b), for example, during the second transaction, the display may display a second authentication image with the same set of dots (a)-(i) as in the first authentication image shown in a). However, in the second authentication image shown in a), the dots (a), (d), (g), and (h) are at different positions than the positions shown in the first authentication image in a). The user may enter a second glyph into the phone to connect the dots (a), (d), (g), and (h). Because the dots (a), (d), (g), and (h) in the second authentication image are at different positions than in the first authentication image, the second glyph has a different configuration than the first glyph .
Similar to the authentication of the first glyph, the second glyph is verified for accuracy.
Although first and second glyphs and first and second transactions are discussed herein in the context of two consecutive transactions, it is understood that many more glyphs and transactions can be used in other embodiments of the invention.
The authentication images in a) and 4(b) comprise arrays of two dimensional objects such as dots. Other two-dimensional image elements include streets or landmarks in maps, walls of mazes, etc. When successive authentication images are presented to the user in successive transactions, the image elements in those authentication images change positions or change in some other way. For example, different authentication images may be rotated with respect to each other, may have different sizes with respect to each other, may be shifted relative to each other, etc.
Maps can be particularly useful as authentication images. For example, an authentication image may include a map that the user is intimately familiar with. For example, the map may include the user's home location and the user's work location. The user may know his preferred route from home to work, and back to home. This path could form the user's authentication glyph. The orientation of the map (e.g., right-side up, and then up-side down) could change with each transaction, so that the configuration of the entered glyph changes for each transaction. Another example of a useful map may be a map of a recreational site (e.g., an amusement park) that the user frequents. For example, the map may be a map of Disneyland. The user's authentication glyph may be the preferred ride sequence that the user takes through Disneyland.
Embodiments of the invention have a number of advantages. First, because the image elements in the authentication images that are used to authenticate a user during a transaction change, the glyphs that are entered into devices used by a user are constantly changing. Unlike an ordinary signature, this makes it much more difficult for an unauthorized person to replicate, and therefore use in an unauthorized manner. For example, even if an unauthorized person intercepts an electronic signature from a user's phone or computer, the data representing the signature would be of little value. Unlike a static signature, it could not be used again in a subsequent transaction, since the actual glyphs received by the device have different configurations for different authentication images. Second, if a remote server computer changes the authentication images in a predetermined or random way, the unauthorized person would not be able to reproduce the correct glyph, even if the consumer's portable consumer device is stolen. Third, embodiments of the invention have advantages over biometric authentication mechanisms. For example, complex electronics are not required in embodiments of the invention, but are required in biometric authentication mechanisms. Further, with biometrics, once biometric data are stolen, the biometric data can be reused. In contrast, in embodiments of the invention, if a person steals a glyph during a transaction (e.g., by looking at the user while the user creates the glyph), the glyph will not be used to authenticate the user during the next transaction so the stolen glyph is useless.
Specific embodiments of the invention further details regarding embodiments of the invention are provided below. shows a system which can be used in embodiments of the invention. Note that embodiments of the invention may use all or only some of the components shown in .
Additional embodiments of the invention are discussed in detail below.
I. Systems
shows a system 20 that can be used in an embodiment of the invention.
The system 20 includes a first merchant (“A”) 22 and an acquirer 24 associated with the first merchant 22. The first merchant 22 may be a traditional merchant that the consumer 30 can physically go to conduct a transaction. The first merchant 22 may operate an access device 34, which may be in communication with a payment processing network 26. The payment processing network 26 may be in communication with an issuer 28. The issuer 28 can either issue the portable consumer device 32 or an electronic token (such as an electronic payment card) that is stored in the portable consumer device 32 to the consumer 30.
The system 20 can also include a second merchant (“B”) 44, which may communicate with the consumer 30 via the Internet 38. Second merchant B 44 may have a server computer 44(a), which may operate a host site 44(a)-1. The consumer 30 can use a consumer device 40 to conduct transactions with the second merchant 44 by contacting the host site 44(a)-1 via the Internet 38. The consumer device 40 may comprise an authentication module 40′.
Each of the components in is described in further detail below.
The consumer 30 may be an individual, or an organization such as a business that is capable of purchasing goods or services.
The portable consumer device 32 may be in any suitable form. For example, suitable portable consumer devices can be hand-held and compact so that they can fit into a consumer's wallet and/or pocket (e.g., pocket-sized). Examples of portable consumer devices include cellular phones, personal digital assistants (PDAs), pagers, etc. The portable consumer devices can also be debit, credit, or stored-value devices.
The portable consumer device 32 may comprise an authentication module 32′. It may comprise hardware and/or software for facilitating the authentication process. For example, it may comprise code for storing previously registered authentication glyphs, code for sending a received authentication glyph to a remote server computer, etc.
The consumer device 40 may be a portable consumer device 32. Alternatively, the consumer device 40 can be non-portable in nature. For example, the consumer device 40 could be a kiosk or stand alone computer terminal that is not ordinarily moved. It may also comprise an authentication module 40′, which may have similar functions and/or characteristics as the authentication module 30′.
The consumer device 40 or the portable consumer device 32 may comprise a computer readable medium and a display coupled to a processor. The computer readable medium may comprise (i) code for displaying a first authentication image comprising a plurality of image elements comprising a set of image elements, wherein the image elements in the set of image elements are located at a first set of positions on a display screen, (ii) code for receiving a first glyph having a first configuration corresponding to the set of image elements from a user while the first authentication image is displayed, (iii) code for displaying a second authentication image comprising the plurality of image elements comprising the set of image elements, wherein the image elements in the set of image elements are located at a second set of positions on the display screen, wherein the second set of positions is different than the first set of positions, and (iv) code for receiving a second glyph having a second configuration corresponding to the set of image elements from a user while the second authentication image is displayed. It may also have code for providing a first indication that the first glyph is or is not considered authentic, and code for providing a second indication that the second glyph is or is not considered authentic.
In other embodiments of the invention, the consumer device 40 or the portable consumer device 32 may comprise a computer readable medium and a display coupled to a processor. The computer readable medium may comprise code for displaying a first image element, receiving a glyph, wherein the glyph is created by moving the first image element from a first position relative to a second image element to a second position relative to the second image element, and code for sending an authentication message comprising data representing the glyph to a service provider.
The payment processing system 26 may include data processing subsystems, networks, and operations used to support and deliver authorization services, exception file services, and clearing and settlement services. An exemplary payment processing system may include VisaNet™. Payment processing systems such as VisaNet™ are able to process credit card transactions, debit card transactions, and other types of commercial transactions. VisaNet™, in particular, includes a VIP system (Visa Integrated Payments system) which processes authorization requests and a Base II system which performs clearing and settlement services.
The payment processing system 26 may include a server computer 26(a) operatively coupled to a database 26(b). A server computer is typically a powerful computer or cluster of computers. For example, the server computer can be a large mainframe, a minicomputer cluster, or a group of servers functioning as a unit. In one example, the server computer may be a database server coupled to a Web server. The payment processing network 26 may use any suitable wired or wireless network, including the Internet.
The server computer 26 may operate a host site 26(a)-1. The host site 26(a)-1 may allow the consumer 30 to select or upload authentication images, and may allow the consumer 30 to manage an account.
The server computer 26(a) may also comprise an authentication module like the authentication module 32′ in the portable consumer device 32.
As noted above, the first merchant 22 may also have, or may receive communications from, an access device 34 that can interact with the portable consumer device 32. The access devices according to embodiments of the invention can be in any suitable form. Examples of access devices include point of sale (POS) devices, cellular phones, PDAs, personal computers (PCs), tablet PCs, handheld specialized readers, set-top boxes, electronic cash registers (ECRs), automated teller machines (ATMs), virtual cash registers (VCRs), kiosks, security systems, access systems, and the like.
If the access device 34 is a point of sale terminal, any suitable point of sale terminal may be used including readers such as portable consumer device readers. The card readers may include any suitable contact or contactless mode of operation. For example, exemplary card readers can include RF (radio frequency) antennas, magnetic stripe readers, etc. to interact with the portable consumer devices 32.
In a typical purchase transaction in a portable consumer device-present type of transaction, the consumer 30 purchases a good or service at merchant A 22 using the wireless portable consumer device 32 such as a mobile phone. The consumer's wireless portable consumer device 32 can interact with an access device 34 such as a POS (point of sale) terminal at merchant A 22. For example, the consumer 30 may take a wireless phone and may pass it near a contactless reader in a POS terminal.
An authorization request message is then forwarded to the acquirer 24. After receiving the authorization request message, the authorization request message is then sent to the payment processing system 26. The payment processing system 26 then forwards the authorization request message to the issuer 28 of the portable consumer device 32.
After the issuer 28 receives the authorization request message, the issuer 28 sends an authorization response message back to the payment processing system 26 to indicate whether or not the current transaction is authorized (or not authorized). The transaction processing system 26 then forwards the authorization response message back to the acquirer 24. The acquirer 24 then sends the response message back to merchant A 22.
After the merchant 22 receives the authorization response message, the access device 34 at the merchant 22 may then provide the authorization response message for the consumer 30. The response message may be displayed by the POS terminal, or may be printed out on a receipt.
In an Internet-based type of transaction, the consumer 30 may log onto the merchant's host site 44(a)-1, and may purchase items using the consumer device 44(a), which may be a personal computer with a standard Internet browser and operating system such as a Windows™ based operated system. The server computer 44(a) operated by the merchant 44 may send the authorization request message to the issuer 28 via the payment processing network 26. As in the portable consumer device-present type of transaction, the issuer 28 approves or declines the transaction, and an authorization response message can be sent to the merchant 44, and eventually to the consumer 30 via the consumer device 40.
The authentication processes described herein can be used in both portable consumer device-present types of transactions, as well as Internet based purchasing methods. Glyph authentication processes can be performed using a portable consumer device, consumer device, and access device.
At the end of the day, in both the portable consumer device-present and Internet type of transactions, a normal clearing and settlement process can be conducted by the payment processing system 26. A clearing process is a process of exchanging financial details between an acquirer and an issuer to facilitate posting to a consumer's account and reconciliation of the consumer's settlement position. Clearing and settlement can occur simultaneously.
II. Registration Methods
In some embodiments of the invention, a consumer 30 may register an authentication glyph with a service provider such as an organization that runs a payment processing network 26 or an issuer 28. For example, the consumer 30 may first use the consumer device 40 to contact the host site 26(a)-1 on the server computer 26(a) in the payment processing network 26 (step ). In other embodiments, the consumer 30 can use the portable consumer device 32 to contact the payment processing network directly (e.g., via communication channel 58).
After contacting the host site 26(a)-1, the consumer 30 can select one or more authentication images. There are a number of ways to select authentication images. For example, when the consumer 30 is logged onto the host site 26(a)-1, the consumer 30 can select an authentication image from a library of authentication images on the host site 26(a)-1. Alternatively, the consumer 30 can upload his own private collection of images to the host site 26(a)-1. For example, the consumer 30 may have a picture, pictures, or video of his favorite mountain at his favorite ski resort and this can be uploaded to the host site 26(a)-1 and may be used as the consumer's authentication image. Such authentication images may be stored in the database 26(b).
If the authentication image is to have a three-dimensional object such as a mountain in it, then the consumer 30 may upload at least two images of the object from different perspectives to the host site 26(a)-1. The at least two images may include first and second authentication images. Alternatively, commercially available digital image rendering software can be used to render any missing parts of a three dimensional object using pictures of various objects taken from different perspectives.
The server computer 26(a) may then send a request message to the user's consumer device 40. The request message may ask that the user draw a glyph corresponding to the selected authentication image. Once the user draws the glyph on the consumer device 40, the glyph may be stored in the database 26(b) by the server computer 26(a). The glyph configuration may have a shape corresponding to the set of image elements in the plurality of image elements. This way, the payment processing network 26 can use the stored authentication image and the corresponding glyph to verify that any future data representing the glyph that is received at the server computer 26(b) are authentic. At this point, the glyph is registered (step ) and this may be characterized as an “authentication glyph.” Each time the set of images objects is presented to the user in a different authentication image, then can be rearranged and the server computer 26(a) can verify the authenticity of a received glyph if it corresponds to the particular set of image elements. The glyph and the authentication image may alternatively or additionally stored in an authentication module 32′ in the portable consumer device 32 or in an authentication module 40′ in the consumer device 40. If the authentication glyph is stored locally in the portable consumer device 32 or the consumer device 40, the portable consumer device 32 or the consumer device 40 can verify that the received glyphs correspond to the authentication glyph.
III. Authentication Methods
Authentication methods can be described with reference to , 3, and 5(a) and 5(b).
Referring to , a consumer 30 may first initiate a transaction using the portable consumer device 32 (at step ). The consumer 30 may be shopping for goods at the merchant A 22 and may place the portable consumer device 32 close to or in contact with the access device 34 during the transaction.
Before or after the portable consumer device 32 is placed close to or in contact with the access device 34, the display screen on the consumer's portable consumer device 32 may display a first authentication image (step ).
The consumer 30 may then enter a first glyph into the portable consumer device 32 and the portable consumer device 32 may then receive the first glyph (step ). The consumer 30 may use a stylus or a finger to draw the first glyph on the display screen of the portable consumer device 32.
After receiving the first glyph, the portable consumer device 32 may then send an authentication request message including data representing the glyph to the server computer 26(a). This can be done by communicating directly with the payment processing network 26 (as shown by line 58) using a mobile telephone carrier network or the like. Alternatively, this can be done by sending the authentication request message to the access device 34, which then passes it to the payment processing network 26 via the acquirer 28.
The server computer 26(a) then determines if the received data representing the glyph is authentic by comparing the data to data representing the authentic glyph that is stored in the database 26(b). If the glyphs match or otherwise correspond to each other, then the server computer 26(a) sends an authentication response message back to the portable consumer device 32. This can be done directly through a direct communication channel 58 between the portable consumer device and the payment processing network 26, or through the acquirer 24, merchant 22, and access device 34. If the glyph is determined to be authentic, then the authentication request message may be indicate this and the consumer 30 may proceed with the purchase transaction as described above. If it is not authentic, then the organization that operates the payment processing network 26 can send another authentication request to the consumer 30, or may not allow the consumer 30 to proceed with the transaction.
In other embodiments, an authentication module 32′ in the portable consumer device may perform the authentication functions described above.
At some point in time, the consumer 30 could then initiate a second transaction in the same manner with the portable consumer device 32 (step ). In yet other embodiments, the issuer 28 can perform the functions that the payment processing network 26 are performing.
Before the consumer is allowed to perform the transaction, the portable consumer device 32 may display the second authentication image (step ). The second authentication image may differ from the first authentication image in any suitable way. For example, the image elements in the first and second authentication images can be rearranged, rotated, etc.
After the second authentication image is displayed, the portable consumer device 32 then receives the second authentication glyph from the consumer 30 (step ). As noted above, the consumer 30 may use a stylus or a finger to draw the second glyph on the display screen.
The portable consumer device 32 then sends the second authentication glyph to the server computer 26(a) (step ).
The server computer 26(a) then determines if the received data representing the second glyph is authentic. If it is, then the server computer 26(a) then sends an authentication request message back to the portable consumer device 32, and the portable consumer device 32 receives this message (step ). If the glyph is determined to be authentic, then the authentication request message may be indicate this and the consumer 30 may proceed with the purchase transaction as described above. If it is not authentic, then the organization that operates the payment processing network 26 can send another authentication request to the consumer 30, or may not allow the consumer 30 to proceed with the transaction.
In some embodiments, a separate authentication request message and authentication response message may not be respectively sent and received. In some embodiments, an authentication request and response may be respectively included in a traditional authorization request message and a traditional authentication response message.
The first and second authentication images in a) and 4(b) include images of two-dimensional objects. In other embodiments, the authentication images can include images of three-dimensional objects. This is illustrated in a) and 5(b). Compared to glyphs drawn relative to two-dimensional image elements, glyphs drawn on three-dimensional image elements are much harder for an unauthorized person to break, since an additional layer of complexity is provide by the three-dimensional nature of the object depicted.
The first authentication image in a) shows a ski resort. This authentication image may be displayed on the display screen of the user's portable consumer device when the user conducts a first transaction. The ski resort includes a number of towers , , , , , . Ski lift cables , , , and are strung between pairs of adjacent towers , , , , , . Other objects including rocks , , and ski lodges , are also shown. A number of ski paths , , , , are also shown in a). The various objects (e.g., the slope of the mountain, the rocks, etc.) in a) can be three-dimensional image elements.
When conducting a first transaction, a user may draw a first glyph relative to the objects in the authentication image shown in a). The first glyph may represent a preferred ski path typically taken by the user when the user visits the ski resort. For example, the user may typically take the ski lift from tower , to tower , to tower , and then down path to ski lodge . The image elements , ,
| منتديات فلور ارت |
| هل تريد التفاعل مع هذه المساهمة؟ كل ما عليك هو إنشاء حساب جديد ببضع خطوات أو تسجيل الدخول للمتابعة. |
Admin
المساهمات : 50
تاريخ التسجيل : 14/01/
الموقع : cromwellpsi.com
4GL Interactive Debugger VUC6 s/n: MET#A Key: TYWOMF 4GL Rapid Development System Run Time Facility VUC6 s/n: MET#A Key: TYWOMF 4GL Rapid Development System VUC6 s/n: MET#A Key: TYWOMF 4GL VUC6 s/n: MET#A Key: TYWOMF 4Screens v Name/Company: (Anything) s/n: 4Screens v Name: cromwellpsi.com [WkT!99] Company: Whiskey kon Tekila s/n: 4Screens V Name: Nemesis] Company: tnt s/n: 4ScreensV Name: cromwellpsi.com [WkT!] Company: Whiskey kon Tekila s/n: F 4- Sight Fax v s/n: (5 Users) 4- Sight ISDN Manager v s/n: 4Tek WebDB v s/n: NS Digital Key: 7CF5-B8AD 4th Dimension Server v s/n: 4th Dimension SQL Server v s/n: 4th Dimension V s/n: D or s/n: D or s/n: H or s/n: X 4th Dimension v s/n: or s/n: or s/n: or s/n: or s/n: or s/n: 4th Dimension v s/n: 4th Dimension vJ s/n: 0AED 4th Right : V 4th Right s/n: V 4Winds Name: Riz la+ s/n: 4W 5 Card Poker Collection V s/n: 5 Card Poker Collection V s/n: 5 Card Stud Poker V s/n: 5 Dices V Name: Team ElilA s/n: 5 Or More Va Name: (Anything) s/n: 5 Star Word Engine V Name: REAL s/n: 5 Star Zip V Name: CROSSFIRE ROCKER s/n: CYLDKJFWVUEXCNA 5 StarZIP V Name: NEMESIS] s/n: LFGFGJNEBFWHRHM Cards V s/n: or s/n: Supreme v Name: Shadowgeist s/n: or Name: Pretty Good Pirate s/n: 5D PDF Creator v s/n: AWCC5CC 5D PDF Creator V s/n: AW15CC5Cd 5PM Term v s/n: AICDBP-HHIJLD-FPTAJF-IBHBIM 5PM Term v s/n: SAB-NECGBC-DNIBTB-TNGENM-EGDBLJ 5PM Term V s/n: ATTT-DDLB-PLIM-MBBI-CAAC-FTFCL Pro Internet Server 32bit va Name: BiGBLUE Company: BLiZZARD s/n: Pro Edu Pro LAN Suite V s/n: LSAUE9 Pro LAN Suite v s/n: LSAH60I Pro Messaging Server vb Server: MSP-MMF34T More-Users: AAI-MMZUP9 Pro Messaging Server vc Server: MSP-MMF34T More-Users: AAI-MMZUP9 Pro Office Server va : Setup: UOS-MMX4DP Users: AAI-MMZUP9 Pro PC Search Vb s/n: PAGOGO Pro PC Suite Vb s/n: PCSM5 Pro PC Suite v99a s/n: PCSFFM9 Pro PC Suite v99a s/n: PCSFFM9 Pro Personal Office Server vb s/n: POSG4A0 Pro Personal Office Server Vb s/n: POSVI7Z Pro Personal Office Server Vc s/n: POSP37D Pro Plus Pack 99 va s/n: PPPAB Pro Plus Pack Vb s/n: PPYH8G Pro Web Forum vg Unlimited-Users: WBF-MME5N1 68HC11 Simulator Toolbox v : Name: nico kamminga Company: HE Key: ATIOkkme s/n: 7 Tuner v s/n: DGNUTI Slots v : s/n: Slots V s/n: 8 Ball Deluxe : ZJLFDN5TMAJ 8 Ball Deluxe v s/n: EM or s/n: EM or s/n: EM 8 Ball Slots Suite Code: 8 Ball Slots v Code: 8 Ball Slots v s/n: Retriever V s/n: 64c9-f1ff7b9 20 Retriever V for Outlook s/n: B0FAAC 88 Edit v Name: Cali KAC s/n: 8Leg Web Studio Name: LordByte in Company: #cracking s/n: E 8Tuner v3.x.x Name: Inpher s/n: TNRAPP 98lite Pro V Name: 98ProUser Password: 98Pe71SwPW5S Key: 9hTr4-jW3fdH-qwMY54z 98lite V Millennium Edition s/n: JrspRwMzKp License: Password: aqjifmnq 9Lives v build : s/n: 9x MetaMagic v s/n: MM 9x WebSpider v : Standard: GBU Pro: HO 9xWebSpider v : Standard: GBU Pro: HO A Better Finder Attributes vx Name: Inpher s/n: ABFA-dtrbtdwf-bxxt A Better Finder Creator and Types v Name: FRAGIL s/n: ABFCT-qwtrew-bxhg A Better Finder Creator and Types v1.x Name: Inpher s/n: ABFCT-gwtrew-bxhg or Name: MoonDark s/n: ABFCT-gwtrew-bxhg A Better Finder Rename v : Name: Wicked s/n: ABFR-lqketr-rept A Better Finder Rename v1.x Name: Macintosh s/n: ABFR-lqketr-rept or Name: Server Surfer s/n: ABFR-lqketr-rept A Better Finder Rename v Name: The Zozo s/n: ABFR-lqketr-rept A Better Finder Select v Name: Macintosh s/n: ABFS-cpxtrt-traw or Name: MoonDark s/n: ABFS-cpxtrt-traw A Better Finder Select v Name: Wicked s/n: ABFS-cpxtrt-traw A Day at the Beach slots V s/n: A Day in the Life v Name: BerSerkA s/n: BClaDiTLB A Day in the Life v Name: BerSerkA s/n: BClaDiTLB A Musical Generator v s/n: Beta Tester A Musical Generator V Name: McClain Company: UCU s/n: A Musical Generator v s/n: A Plus Exam Prep V Name: Melborn [iTN] s/n: A Plus Screensaver Creator V s/n: 2XA A Plus Screensaver Creator V s/n: 2XA A Plus Web ScreenSaver V s/n: FCX or s/n: XKM A Real Validator Name: Registered[Faith] s/n: A Real Validator V Name: cromwellpsi.com [AmoK] s/n: or Name: Chamson s/n: A Rob Fantastic MP3 Encoder v Name: sn00pe[evc] s/n: A Smaller Gif v Name: Fatigued s/n: YYYVDC7YCUYY6C5A A Smaller Gif v Name: RAGGER/CORE s/n: YYY9W27Y!UYYY9MT A Smaller Gif v Name: MoWAX [Nobliege] s/n: or Name: RAGGER/CORE s/n: YYY9W27Y!UYYY9MT A Smaller Image v Name: tKC/CiA '98 s/n: A Smaller Note 99 v Name/Company: TEX99 s/n: A.I.D. V s/n: KVJ4E0T A+ Certification Theory Study Guide Code: s/n: ic A1 E-Mail Address Extract V s/n: PCSPK A1 E-Mail Address Pro V s/n: PRMXT A1 Quick Tray v s/n: QKD A1 Wallpaper Pro v : s/n: D9a72gKL39 A Attack v s/n: or s/n: A Attack v s/n: or s/n: or s/n: A Attack v s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: A Cuba v1.x s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: or s/n: A1-Image screensaver v : s/n: B5K7ij49p2 A1Monitor V Code: Y A1Monitor v s/n: G A1Monitor v s/n: K A1Monitor V s/n: D A1Monitor V s/n: Y A1Monitor V s/n: O A1Monitor V s/n: S A1Monitor V s/n: S A1Monitor V s/n: Y A1Monitor V s/n: Y A1Monitor V s/n: Y A1Monitor V s/n: Y A1Monitor V s/n: Y A1Monitor V Name: maniacs@cromwellpsi.com s/n: Y A1Monitor V Name: maniacs@cromwellpsi.com s/n: Y A1Monitor V Code: Y A2Z Gradebook Name: UNICITY s/n: A2Z Gradebook Name: Crystal s/n: A2Z Hangman v Name: Crystal s/n: A2Z Hangman v Name: Crystal s/n: A3E v1.x (edit cromwellpsi.com) : line #1: REGNAME=The Bozo Construction Companyline #2: BDAAABABA29 AA Scripter V s/n: alicyb AAA Audio MP3 Maker V Name: DiSTiNCT s/n: AAA FTPeasy V Name: Shaligar^Lash s/n: or Name: NUKEM s/n: AAA MP3 CD Maker V Name: regsoft s/n: AAA Screen Capture V Name:[F4CG] s/n: RQQQ1Q1QQQ AAApeg Image Browser v Name: MisterE [iNSiDE] s/n: Aardvark in a Box Gold V s/n: RGGB78 Aardvark v Name: SiLicon Surfer PC'97 s/n: A6F0C or Name: Phrozen Crew s/n: 1BC68 AB Complete Ping V Name: The Netmech^LasH s/n: dHb AB File Encryptor V Name: The Netmech^LasH s/n: PuP or Name: Norma Blood s/n: PuP AB HTML Compressor V Name: The Netmech^LasH s/n: OpC or Name: Norma Blood s/n: OpC AB Safe Deletion V Name: The Netmech^LasH s/n: AHS or Name: Norma Blood s/n: AHS AB Screen Locker V Name: Norma Blood s/n: AMS AB Screen Locker V Name: The Netmech^LasH s/n: AMS AB System Spy V Name: Norma Blood s/n: ABS AB System Spy V Name: The Netmech^LasH s/n: ABS Abacus Help Desk V Name: (Anything) s/n: Abacus Help Desk V Name: (Anything) s/n: Abacus Law Office Calendar System : s/n: F Abacus V Open Word, go Tools, then on Macro. Now click on the copyright text and enter: s/n: 65JK49 Abalone v s/n: Abaqus Helpdesk Master V Name: (Anything) s/n: Abatus Mirror Server v Name: Dracs Company: Crystal s/n: FCFE Abatus Mirror Server v Name: tarq@ORiON Company: ORiON s/n: 0A03DB6 ABC 95 v s/n: FCCF2B ABC Flowcharter v for Windows : ABC Puzzles v s/n: ABC ToolKit v s/n: ABC ToolKit v s/n: ABCalculator V Name: DemonNite s/n: ABCalculator V Name: DemonNite s/n: or Name: Sempai^LasH s/n: or Name: Mackoi s/n: ABCEncrypt V s/n: B (Serial number must be typed, not pasted!) AbcLotto v s/n: AbcMonitor V Name: fred the hamster Lz0 s/n: 71CNWNRCWRHN ABCPix V Name: DiABLO [ORiON] s/n: ABCPix V Name: GARFiELD [rA] s/n: ABCPix V Name: PiTcH_SiLoW s/n: or Name: MackOi DBC s/n: ABF Value Converter V s/n: 0GU17Qu8xBY6qDKtSQFzOZDOVOcOlPziuHBeR+HA/YUtkZNW7efClXCQBljjeZB/ 10ib4Ok+nOZ8ghEnHithldXHo90Hl1OandyceQilW0yWwI43mb wYOTWumKr7ylf+Ky0DW7Jx5JsfstDe4YEzjtYnDd5ih8IlmGYk DMX9i8l4= Ability Database v98 s/n: NS Ability Office V Name: Nemesis] Company: TNT s/n: Ability Office V s/n: Ability Office Final Retail s/n: AbirNet SessionWall v3 s/n: D1FBBC-6E43AE Key: Abix v Authorization : Company: PGC Name: CYPHER X Address1: Happy Street Address2: (Blank) Address3: Nashua Address4: Oh Phone: Fax: Email: cypherx@cromwellpsi.com License : | |
Admin
المساهمات : 50
تاريخ التسجيل : 14/01/
الموقع : cromwellpsi.com
Adobe Type Manager v for Windows AWWP AdoBe Wild Type s/n: FHWR A-Dock V s/n: A-Dock V Name/Company: (Anything) s/n: A-Dock V1.x Name: HotSix s/n: A-Dock V German s/n: AUQG or s/n: PKFK A-Dock V s/n: or s/n: A-Dock V s/n: DOCK A-Dock V s/n: KRAK Adpinxi V Name: MackOi Company: DBC s/n: M2BRI57Q Adplan Promotional Business Software v s/n: NS Key: E27A ADR V s/n: ADRWPE Adrem Server Manager v s/n: TAY Adrem Server Tools v s/n: PFV Adrenaline Charts Numbers s/n: CHDVMX (Charts) or s/n: NBMDMP (Numbers) Adrenaline Charts Pro v : s/n: CPMW Adres Wijzer v s/n: AD Adress Organizer Va Name: macbain2k s/n: Adressen V Name: DooMdaStic[tCA] s/n: Adresses French v Name: HarvestR CiA 98 s/n: 12 Code: HDZKCB Adressi Bilingual V s/n: MHZKSL1-ADR20 Adressi V s/n: MHZKSL1-ADR20 Adreva 98 v Name: BLiZZARD98 s/n: AD AdrLTReg v Name:vots s/n AdScape32 v s/n: AdsGone V Email: maniacs@cromwellpsi.com s/n: J ADSGone V Name: maniacs@cromwellpsi.com s/n: Y ADSGone V s/n: F AdsOff Name: LoungeAct s/n: 92p8uGb0 AdsOff v Name: TRPSRULEZ s/n: 82K8POM9 AdsOff v Name: 0MisterE[iNSiDE] s/n: 12d45+o AdsOff v Name: CHENZY s/n: 11@22U3 or Name: Gordon s/n: 11m22Bj3 AdSubtract Pro V Name: Recca [DAMN] s/n: DAMN-UVGI-GXEQ9 AdSubtract Pro V Name:Free User CodeAMN-8C9H-KLL3-CWCQ AdSubtract Pro V Name: Howard F Mulvaney s/n: ADZG-4BW5-PZAV-M7R3 Adult Poker v Name: MrGReeN Company: WKT s/n: AP AdultPromoter v s/n: ADL Advance Dialer Bit name:PANK s/n Advance Dialer v Name: PANK s/n: Advance Site Position V s/n: ASP-D2MLRX42BDGDWK Advanced Access Password Recovery V Run the program with 'ACPR /register' and enter: Code: 8KCApk6PrrhVr7ZsrfG8bese Advanced Access Password Recovery V s/n: 8KCApk6PrrhVcBCnwxfz2S3t Advanced Access Password Recovery V s/n: 8KCApk6PrrhV87gfxeftwsqm Advanced ACE Password Recovery V s/n: ACEPAPDTYAHHTPQUXQTB Advanced ACT Password Recovery V s/n: ACTPWGYTE Advanced ACT Password Recovery V s/n: ACTPAMVHA Advanced Administrative Tools v Name: TRPS s/n: DCFDC Advanced Administrative Tools V Name: JudgeD [PC'99/MFD] s/n: CCA Advanced Administrative Tools V Name: Orion s/n: DCFBB Advanced Aircraft Analysis and Design Password: Cessna Advanced App Saver V Name: Licensed User Company: Licensed Company s/n: 0f5a27c0 Advanced Application Saver V Name: Team iTR Company: iNTEGRiTY s/n: 1dfe0 Advanced Archive Password Recovery V Name: Juan Lozada s/n: ARCHPR-TBHW5SSMYGQS-CUQ9SNYDE59T4KMM Advanced Archive Password Recovery V s/n: ARCHPR-TBHW5SSMYGQS-N5ZDCNUFNX5XBCD4 Advanced ARJ Password Recovery V s/n: AGBdYfPNaakYvwmNVKNMYveD Advanced Auction Builder V s/n: 10E52FFBl5aW Advanced Batch Converter V Name: (Anything) s/n: Kl-HGFHGH^fg6 Advanced Batch Converter V s/n: Fg56+H? or s/n: Kl-HGFHGH^fg6 or s/n: htyfFGG#d Advanced Batch Converter V Name: (Anything) s/n: halyava#1 Advanced Batch Converter V Name: Kelly Nash s/n: halyava#1 Advanced Calculator V s/n: JPRN Advanced Color Selector V s/n: DRKKL or s/n: FCDDB Advanced Converter Pro V Name: Corbio s/n: License: 5A4BACDCB Advanced Development System v s/n: E87 Advanced Dialer v Name: BIGBLUE! s/n: 7D5E6F00 or Name: THE KEYBOARD CAPER s/n: 73B70D00 or Name: TKC/CIA '98 s/n: 2D Advanced Dialer v Name: THE SCYTHE s/n: F or Name: Name: CoKeBoTtLe99 s/n: F1A00 Advanced Dialer v Name: p00p tERTz Company: SPYDER! s/n: C66F Advanced Dialer V Name: CZY s/n: D5C00 Advanced Dialer V Name: FREE USER s/n: 4F Advanced Dialer V Name: FREE USER s/n: 4F Advanced Direct Mailer V s/n: ADRKEJZK Advanced Direct Remailer V s/n: ADRMTHYJ Advanced Direct Remailer V s/n: ADRJMHPG Advanced Direct Remailer V s/n: ADRKEJZK Advanced Direct Remailer V s/n: ADRJZNMH Advanced Directory Comparison and Synchronization V Beta Name: Hazard s/n: Advanced Directory Comparison and Synchronization V Name: BaND [SCT] s/n: AB47F63E Advanced Directory Comparison and Synchronization V Name: TEAM ElilA s/n: F64EF Advanced Disk Catalog v Beta 2 s/n: ERqdY0pQRs2KIUvI Advanced Disk Catalog v s/n: MbMDYnJHUASF2Ub Advanced Disk Catalog Va s/n: MbMDYnJHUASF2Ub Advanced Disk Catalog V s/n: mQso5PedAMmh0k Advanced Disk Catalog V s/n: MbMDYnJHUASF2Ub or s/n: mQso5Pax9RDYlf Advanced Disk Catalog V s/n: E3yUyUJdZGE1umXm Advanced Disk Catalog V s/n: MbMDYnJHUASF2Ub Advanced Disk Cleaner v Name: Shaligar^Lash s/n: Advanced Email Extractor V s/n: AEEQUNKR6R7ECYG Advanced Email Extractor V s/n: AEEEA6YF3P7TAAT Advanced Email Extractor V s/n: AEEUKXENYCTYCGQ Advanced Email Extractor V s/n: AEEKFYV9KG9 Advanced Email Extractor V s/n: AEEA3QEGFCTH5PZ Advanced Evaluator V Name: Crudd [TeX] s/n: 5DAACCA Advanced Evaluator V Name: cromwellpsi.com [WkT!] s/n: EEAE Advanced Evaluator V Beta Name: TEAM ElilA s/n: 90EBBAC4F31 Advanced Evaluator V3.x Name: +DzA kRAker (Regele Piratilor) s/n: 20DB7A47B16EF7 Advanced Excel 95 Password Recovery V s/n: ENFEDW Advanced Fabrication v : s/n: Advanced Find and Replace V s/n: aaaaadIQKZFfZodkUBGhdqzeqndtnsTCbQXk4MC+0Jwm45X+BP 0HGwBC Advanced Find and Replace V Name: AFR s/n: aaaaadIQKZFfZodkUBGhdqzeqndtnsTCbQXk4MC+0Jwm45X+BP 0HGwBC Advanced Find and Replace V Name: AFR s/n: aaaaadIQKZFfZodkUBGhdqzeqndtnsTCbQXk4MC+0Jwm45X+BP 0HGwBC Advanced Find and Replace V Name: AFR s/n: aaaaadIQKZFfZodkUBGhdqzeqndtnsTCbQXk4MC+0Jwm45X+BP 0HGwBC Advanced Find and Replace V Name: AFR s/n: aaaaadIQKZFfZodkUBGhdqzeqndtnsTCbQXk4MC+0Jwm45X+BP 0HGwBC or Name: RoBoCoP [iNTENSION] s/n: aaaaaGzZMCux3C0qG96SF9T1cwNGfeDobYiBViIQPxCrdh9k8h dC+VaR Advanced Find and Replace V s/n: pWbp/ CeheikReQMskNpV9krod9lB6ALkVntW+kukwzJ6EHSdkUSRe56 F27EwtgHw1DbSBEO1/ 4j2jQWuwxptYOmj5mzOTl5WJULcNErDT1rN9iX1VFHJjKJd DvtwOzFd/sHYTojSBrebGAuERoMr5fwIhvxknI0MPdAT6Ngg= Advanced Find and Replace V s/n: 0sbt0JJY6rKwl7mLS3tDJ5oWdT7GYCNU6KUwFW+RP9XNzWtK+g vsucrAUYTWfw/ oZ3MB0j6xerOl2UFB8zNpOv8MbwbJLmLR6BolxtasRsS0svMpk 2BTCLh9mU3M7cdvptr9MjJsCGVezLZpIEPBV9qbFArHKFADCBX D3vy/UwUQ= Advanced Find and Replace V s/n: 0XBa9MTUzYQXBpgQqsXEI68rVIanCRnIXu9fG23p5KX3nzUcYa fld9ZJzsSMzmrXujjzlLzws1QQhxrP5ysc7nal8jAngkHpzcG1 NMpuB5/ S9sTFwpK8FX9TKTG3dnO44VeKOdPmzZNKfg3SLjivqam51nFsj mYH/4FtMNX70xAA= Advanced FTP Client V Name: (Anything) s/n: FTPFFF:F::FFFF:: Advanced GIF Animator V s/n: 0qT+7ks91OS6TwwuLvuwXOgnH9C1VSEo9HIWngLCMBIuHEWyJz uGuNjjAVvsQIf8lo8MhU4c6QZfVgfvrKE7u6ZOsdsLI8UGMKEK 3nDr1cRHcvufQ9LTGS3Bz16BSbF7c7cd7gkAFbooFcHO/P8lPfFRTTAg+2Mnrz28OeYhZSIk= Advanced GIF Optimizer v Beta s/n: *uuTTrfb4 or s/n: TYgG Advanced GIF Optimizer V Name: Deborah Glast s/n: aa Advanced Gradient Controller s/n: B4H8-R Code: 2LA Advanced Hardware Editor V s/n: AHEAK Advanced Hardware Editor V s/n: AHEAK Advanced Hardware Editor V s/n: AHEAK Advanced Hardware Editor V s/n: AHEAK Advanced Hardware Editor V s/n: AHEAK Advanced Hardware Editor V s/n: AHEAK Advanced Hardware Editor V s/n: AHEAK Advanced Hex Editor v s/n: Advanced Hosting Controller V s/n: HCDBDA3C9EE Advanced Instant Messengers Password Recovery V s/n: MGPR-8HPY-WP3D-MX6F-AFVBP-UYMV-EJEYD Advanced Internet Tool v Name: BaRT SiMPSoN s/n: 4FCD-E3DD Advanced Internet Tool V Name: JoHnNy s/n: BDAC Advanced Launcher V Start the program. Click run, RIGHT click the toolbar and enter: s/n: 6T7rbz8mA3dyYPj9L1sJJLsp2+K3HAN0BSH98JfHBadrky+MCN t61xyIjSXk7Tpzrjzc5eB49JsyItJ13yXK1eub37ZKk9sR+nqe pLsUcSMkVVLJx4zTr26T6UFcaCcKo4GNgMVKhYIdAbu/tGPmYBF8lXhmPnKiU6NfkoG/S6I= Advanced Link Catalog s/n: sdqZxa8KhHhxdfB5EXKZJrci47UOmCqJHqFDTmOBov8fvsE Qw8FHuK48/YNGbRiRYjZ/ +AbFj1ffL1iA1ci13Nn3Jgur7WJ8nk+NFjqGsCrdJUrGHeEfse NToWhozp6rI5P2fP0J5vDm4htyFchw5/5g5VJR0ytTNyqrzo6Vk= Advanced Lookup V Name: MaP s/n: | |
Admin
المساهمات : 50
تاريخ التسجيل : 14/01/
الموقع : cromwellpsi.com
Advanced Lotus Password Recovery V s/n: ALPRAXQTJ Advanced Maillist Verify V s/n: AMVXFSUN Advanced Maillist Verify V s/n: AMVGRRAX Advanced Mass Sender V Name: SWW //dF s/n: 95EE2CD0 Advanced Mass Sender V Name: Samson s/n: 15C6C7DCB Advanced Mass Sender Vb Name: Oblomis Babka s/n: BA9BFFBA89A07 Advanced MP3 Home Studio V s/n: Advanced Net Tools Pro V English Email: TeamEViDENCE@cromwellpsi.com s/n: 4mqUthf8p1$|]r:mgGHM:LUXQPfPzvGd)T.}YrHw#g5 Advanced Net Tools Pro V English Email: TeamEViDENCE@cromwellpsi.com s/n: 4mqUthf8p1$|]r:mgGHM:LUXQPfPzvGd)T.}YrHw#g5 Advanced Net Tools V s/n: 1*m{ppeN1Dq^xKmEs+iN(Lyo}tLj{EsV`$uu_{/2rhw`~$}^|{;B?y{x.#??u!|^Vët? Advanced News Scroll Java Applet V s/n: advnrr or s/n: coghkr5u8 (universal for Popular Applets Collection) Advanced Newsticker Java Applet V s/n: dpre53erac or s/n: coghkr5u8 (universal for Popular Applets Collection) Advanced Note Tree V s/n: 0y6kUaTd3R2LFxH21pLQux6FGKSY+QwPy2Gw9EFx80FlEIK +hNE/ fbmR3hmamwqnkoA4mfgy1ptkFnDN7S2MO2awD8xcqmyaBIE OO1ufjiJS6pFo6bLuCibyQt3HlhgjeZncVh1+XGUG1tYBE1bio CKyZDqDkis2iBlSsk= Advanced Office Password Recovery Pro V s/n: MSF2K-PBUWMDJ Advanced Office Password Recovery Pro V s/n: MSF2K-PBFSRUP Advanced Office Pssword Recovery Pro V s/n: MSF2K-PBPHUHU Advanced Office 95 Password Recovery V s/n: ODPRSE Advanced Office 97 Password Recovery V s/n: ODNXEN Advanced Office 97 Password Recovery V s/n: OZEVZQ Advanced Outlook Express Password Recovery V Name: James Saska s/n: LEPR-T2K7-NA8Z-3DUE-RHMTS-UQGR-PYVVY Advanced Outlook Express Password Recovery V s/n: LEPR-T2K7-NA8Z-3DUE-BAVHC-JTZM-AVQJG Advanced Outlook Express Password Recovery V s/n: LEPR-T2K7-NA8Z-3DUE-JTXUQ-VECP-PTQCR Advanced Outlook Password Recovery V s/n: OLGVJPN Advanced Outlook Password Recovery V s/n: OLHKKHR Advanced Outlook Password Recovery V S/N،GOLHKKHR Advanced PDF Password Recovery V s/n: PDFPJQCPN Advanced PDF Password Recovery V s/n: PDFPEYSVY Advanced PDF Password Recovery Vs/n: PDFPZTFJU Advanced Project Password Recovery V s/n: MSPPDWMRA Advanced Query Tool V Name: worp [DiSTiNCT] s/n: Advanced Query Tool V Name: ECG s/n: Advanced Query Tool V Name: TZSiSO s/n: Advanced QuickBooks Password Recovery V s/n: QBPRURZBB Advanced QuickBooks Password Recovery V s/n: QBPRURZBB Advanced RAR Password Recovery V s/n: ARPRGWKURGRENWBRQWRY Advanced RAR Password Recovery V s/n: ARPRDBCXPBUUDKCUEENM Advanced RAR Password Recovery V s/n: ARPRDBCXPBUUDKCUEENM Advanced Ra-Renamer V Name: Peri0d s/n: ARR-SVQc2w4P-XUcx5li4 Advanced Registry Tracer V s/n: ARTPHQNS Advanced Registry Tracer V s/n: ARTJSNVC Advanced Replacer V Name: Registered User s/n: gadAUYBd1p Advanced Skeleton for Maya V s/n: Advanced Skelton V For Maya s/n: Advanced Space Hunter V Name: CORE/DrRhui s/n: Advanced Space Hunter V build 74 : Name: SiLicon Surfer PC'97 s/n: or Name: Phrozen Crew s/n: or Name: n03l s/n: Advanced Space Hunter V build 79 Name: Sempai^LasH s/n: Advanced Space Hunter V Name: Bush Jr s/n: Advanced Speed Typing 98 V for Win9x : Name: dustie of blizzard Code: c Advanced Speed Typing Tutor V Name: (Anything) s/n: aerop or s/n: c or s/n: c Advanced Speed Typing v Name: dustie of blizzard s/n: c Advanced Speed Typing v Name: TRPS s/n: aerop Advanced Speed Typing v Name: dustie of blizzard s/n: c Advanced Speed Typing V Name: (Anything) s/n: aerop or s/n: c or s/n: c Advanced Speed Typing V s/n: aerop or s/n: c or s/n: c Advanced Tetric V Name: Jane Glow s/n: A4LC-VYT5-QASU-QSW4-L4 Advanced Text Editor v s/n: atevwgs2otr2-wg Advanced Typewriter Scroll Java Applet V s/n: typws or s/n: coghkr5u8 (universal for Popular Applets Collection) Advanced VBA Password Recovery Pro V s/n: VPVRBYU Advanced VBA Password Recovery Pro V s/n: VPUEZVM Advanced VBA Password Recovery V s/n: VBSXVFD Advanced VBA Password Recovery V s/n: VBHNWJN Advanced Video Poker v Name: dustie of blizzard s/n: Advanced Video Poker v Name: Einhon [Breakpoint] s/n: Advanced Video Poker V Name: fALC0N [DSi] s/n: vd9Yk+rRMd7se2C80 or Name: Hamst [e!] s/n: eExRxk3br8mda1 or Name: TUC PC99 s/n: 0JDSi-len2 Advanced Video Poker V Name: MANiACS s/n: 65qMCmLA1 or Name: cromwellpsi.com s/n: 0y12KMRzoXl0c/uF or Name: Joe Smith s/n: hk/77lnImMMc0 Advanced Video Poker V Working Name: Joe Smith s/n: hk/77lnImMMc0 Advanced Wire EDM v s/n: Advanced Word 95 Password Recovery V s/n: WPANDJ Advanced Word 95 Password Recovery V s/n: WTSPNH Advanced WordPerfect Office Password Recovery V s/n: CRPR-RDVN-RAMJ-VJBX-UFQGH-JPCT-AUXUR Advanced Zip Password Recovery vA : Run command line: cromwellpsi.com /register s/n: TcQdBAYCRlQW95HO Advanced Zip Password Recovery v s/n: tcKxzxKUhzLjuAAD Advanced Zip Password Recovery v s/n: SUfjyXZ97rwMZ2J3 Advanced Zip Password Recovery v s/n: tcKxzxKUhzLjuAAD Advanced Zip Password Recovery v Name: LOMAX s/n: tlc1fahzfUb9n8GaJcCBTsxkHcrNHb8R Advanced Zip Password Recovery V s/n: Nqu5hf6cAjz4U Advanced Zip Password Recovery V s/n: NQG4WsRNDxqFBS9f Advanced Zip Password Recovery V s/n: HmnudxdA2X5gF4Yc or s/n: EEYGvaFBfCqjZWwz Advanced Zip Password Recovery V s/n: vTdrwsyxPQPaStqU or s/n: SjuvbcAezSK2Gg3 AdvancedChecker V s/n: Q93H46X2 AdvancedSkeleton V For Maya s/n: Advantage Database Server V s/n: AuthKey: QGNMQ Advent 98 v Name: Karen E. Caughey Address: Beech Grove, Indiana, USA Code: Adventure Maker v Name: (Anything) s/n: Adventure Maker V Name: ViSiON s/n: Advertisment Wizard V Name: maximum s/n: 2ZLWILR Advocate V Name: MANiACS Company: MANiACS s/n: Advocate Legal Software VAdvocate Name: Sea-you Company: ENFUSiA s/n: Advocate V Name: MANiACS Company: MANiACS s/n: Advox Omnigate v : Go to System button / License tab and enter: Company: PREMiERE thisdomain: premiere@cromwellpsi.com fromdomain: premiere@cromwellpsi.com Key1: JEDCAHDKODJDONAI Key2: KCPALAIMCHNOCKGG AdWiper v s/n: PREDATOR AdWizard V Name: TEAM ElilA s/n: WESAFOWOKOCVRU AdWizard V Name: TEAM ElilA s/n: WESAFOWOKOCVRU AECVIZ Explorer V Name: TEAM SCOTCH s/n: A6G4L3C4T7 AecViz V Name: TaMaMBoLo/EPSiLON/bLACK sQUADRON s/n: S7K7A7O5O7 AECVIZ V Name: Bush Jr s/n: U2R6A5R7R7 AECVIZ V Name: Bush Jr s/n: U2R6A5R7R7 or Name: ECloZion s/n: E7I4L5O4A3 or Name: MaTHieU s/n: U7R6A6U7R7 AecViz V Name: Bush Jr s/n: U2R6A5R7R7 Aelita BootAdmin v2.x s/n: ID1-V2x-USWXME1qAOEh Aelita ERDisk v s/n: IDCORE/Vizion-V-ZHwkDk1r Aelita EventAdmin v s/n: IDCORE/Vizion-V-Klt4ZeHx Aelita Journal v s/n: ID-Vx-ULua7zXZ Aelita MultiReg v1.x s/n: ID1-V1x-USWXwHFf0are Aelita TimeAdmin v2.x s/n: ID1-V1.x-USWXacmWgf97 Aelita Virtuosity v s/n: IDCORE/Vizion-VO9Wzjc Aelite Journal v : ID-Vx-ULua7zXZ Aepryus Calculator V Name: Finn Mac CooL s/n: Aepryus Graph v Email: Nmfist@cromwellpsi.com s/n: Aepryus Suite v Name: CiA s/n: Aesop GIF Animator V s/n: MGVQQV Aestesis 98 v Name:v s/nopo0 Aestesis 98 v Name: herzog antoine s/n: vabixexakibuyi Aestesis v Name:herzog antoine Code:vabixexakibuyi Afficheur de paroles V s/n: Affiliate Keeper V Name: MaTHieU s/n: 5ADAACF53D Affirmative Action DUN v : Name: GZI s/n: 7xxaHx Afranchi V s/n: AfTer Dark +v for Windows : ADW or AD After Dark Atom s/n: ABA After Dark Black Jack s/n: BBJ After Dark Disney (mac) : DIS After Dark Flintstones s/n: After Dark Loony Tunes (mac) : ZQA After Dark Marvel (mac) : EAM After Dark Mighty Atom s/n: ABA After Dark Myst s/n: MSS After Dark Scream Saver (mac) : SSM After Dark ScreenSaver - Disney Edition s/n: DSW or s/n: DSW After Dark ScreenSaver - Loony Toons Edition s/n: ZQA After Dark ScreenSaver - Marvel Comics Edition s/n: MVW After Dark ScreenSaver - Star Trek Edition s/n: BSN or s/n: SPW After Dark ScreenSaver - Star Trek: StarDate s/n: ESW or s/n: LSW After Dark ScreenSaver - Star Trek: The Next Generatios: s/n:BSW or s/n:SPW After Dark ScreenSaver - The Simpsons Edition s/n: ZQW or s/n: ZQW or s/n: KAW After Dark ScreenSaver - The Simpsons Edition: KAW After Dark ScreenSaver - The Simpsons Edition: ZQW After Dark ScreenSaver - The Simpsons Edition: ZQW After Dark ScreenSaver - Totaly Twisted Edition : s/n: BII After Dark ScreenSaver - X-Men Edition : s/n: AD After Dark Simpsons (mac) : ZQM After Dark Snoopy Fun Pak s/n: FPWU After Dark Star Trek (mac) : EAM After Dark Star Trek Posters (mac) : SPM After Dark Star Trek:TNG (mac) : ZQM After Dark Totally Twisted (mac) : TTT After dark v for Windows : AD After Dark v s/n: AD or s/n: ADW or s/n: ADW After Dark V s/n: ADM or s/n: ADM or s/n: ADM or s/n: ADM or s/n: ADM After Dark Vb s/n: ADM After Dark VJ s/n: AMJ After Dark V s/n: ADC After Dark VJ s/n: or s/n: After Dark X-Men (mac) : ZQM After Dark X-Men s/n: ZQM After Dark Yamato s/n: YPM After Effects Bundle Edition v : s/n: EWWR After Effects s/n: After Effects v s/n: XH9-SVJ1-B5K After Effects v s/n: EXX (demo) or s/n: EMW After Effects v s/n: EXXR After Effects vJ s/n: EMJR or s/n: EMJR or s/n: EMJR or s/n: KMJR After Effects v s/n: EMWX ( copies) or s/n: EMWR or s/n: EMWR or s/n: EMWR or s/n: EMWR or s/n: EMWR or s/n: EMWR or s/n: EMWR or s/n: EMWR After Effects vb s/n: EXXXX After Effects vb48 s/n: EXXR or s/n: EXXX After Effects vJ s/n: EMJR After Effects V Retail s/n: EWWR After Effects V s/n: EWWR After Effects V Beta s/n: EXXX After Effects V s/n: EWEA After Tune V Name: GARFiELD [rA] s/n: AfterCam V Name: TEAM ElilA s/n: AQEEESYUMSCWGGQAGSEGW or Name: Shockwave s/n: YUYOUKKWMKYGGEMCKIKYK AfterCam V Name: TEAM ElilA s/n: AQEEESYUMSCWGGQAGSEGW AfterCam V Name: Sponge Uk/tCA s/n: KSQIAUIOMYKCGGUSUAYIS AfterCam V Name: TEAM ElilA s/n: AQEEESYUMSCWGGQAGSEGW AfterCam V Name: Nemesis] s/n: ASKUMQWUOMEWIWASYQQCY AfterCam V Name: LAXiTY s/n: slajwfcdmxypwdwzahwhw AfterFX v s/n: EWWR AfterHour V Name: ECLiPSE s/n: ACFDC54FAAC4CB44CDB22C17C5D1A20D4BBC0CBD6AE9A4E 2E21C1C3A3AF4F4F2F2ACAC8A8AC83BCCA43F5AFDDA92EC L AG-Depot V Name: pSB [AmoK] s/n: Age of Dinosaurs 3D s/n: or s/n: Agency DataBase vc s/n: ADW Agenda 98 V Name: Finn Mac CooL s/n: 77FCEFB99EA59A90 Agenda MSD Vj Name: FREELAND EMS s/n: luC7-VG2g-R3uQ7i-a5FT | |
Admin
المساهمات : 50
تاريخ التسجيل : 14/01/
الموقع : cromwellpsi.com
Abix V Name: team embrace s/n: abcdef Abix V Name: Bush Jr s/n: Ablaze Starters vd s/n: MAILEXSTONES Ablaze Starters v s/n: ROCKSDAG Ablaze Web Auto-Promotion v : s/n: AATY (Case Sensitive) Abobe PageMill v s/n: MLWR AboutFace s/n: Above Beyond 98 Name: ThE STaRDoGG CHaMPioN [PC] s/n: CET Above And Beyond V Name: Nemesis] s/n: ZHJ Above And Beyond V Name: cLUSTER / dSI! Pro: qdy or ehw or Lite: ntv or arw Above And Beyond V Name: REFORM s/n: bcw Above And Beyond v : Name: knoweffex DNG s/n: dup Above And Beyond v Name: knoweffex DNG s/n: dup Above And Beyond v Name: zaarnik [BLiZZARD] s/n: CWE Above Black Book v Name: (Anything) s/n: b9v8b9l5k71 Above Black E-Book v Name: (Anything) s/n: b9v8b9l5k71 Above Disk+ va s/n: Above the Rim V for Win9x : Name: dustie of blizzard Code: $7BB or Code: $F Above the Rim v Name: BerSerkA s/n: $F91B Abox V Name/Password: (Anything) s/n: PCR Abracadabra v Name: jog [DNG] s/n: Abracadabra v Name: ARNOLD MOORE s/n: Abracadabra v Name: $keve s/n: Abracadabra v Name: TEAM ORiON s/n: or Name: cromwellpsi.com [WkT!99] s/n: Abritus Business V Name/Company: (Anything) s/n: Abroad! s/n: Absoft Fortran Pro v s/n: Absoft Fortran v s/n: ABSOFT Pro Fortran V S/N،G Absolute Accessories V s/n: Absolute FTP v beta 6 Name: CORE/JES Company: CORE s/n: Expiration: never Key: Absolute FTP v RC 11 Name: _RudeBoy_ Company: Phrozen Crew s/n: Expiration: Never Key: Absolute Menu Java Applet V s/n: amenu27b47 Absolute On line v name: ls-Warp98 s/n: Absolute Protect v Name: ZOBEL s/n: Absolute ScreenSaver Changer V Name: Kent/CORE s/n: D41B78A Absolute Security Pro V Name: C0ke s/n: GPBKTCNKYZKWQPJ Absolute Security Pro V Name: Demian/TNT! s/n: LGYCNAPBYWAJNUR Absolute Security Pro V Name: CROSSFIRE ROCKER s/n: JDHULALBFRHMLQY or Name: FIREANGEL [EVD] s/n: NVMFTMKNPTUCHJA Absolute Security Pro V Name: NSA_CRACKERZ_TEAM s/n: UGQCRLAHKEFXPYW Absolute Security Standard v Name: jog [DNG] s/n: BTAYNNNNYPEGTPK Absolute Security Standard v Name: escom/CORE s/n: BGUPFVLRUPAKTTG Absolute Security Standard v Name: i am sexy s/n: HYVHAAVNNCMUMJE Absolute Security Standard v Name: Delphic s/n: VQZUKKXMGWRKRFA Absolute Security Standard v Name: CoKeBoTtLe99 s/n: CKNMAGKDQCYUFND or Name: Mr_GReeN [WkT!] s/n: GYEARKGZPKNBGNW or Name: Raybiez Cracking s/n: KDYCBZAJKVUMJWE Absolute Security Standard V Name: SkUaTeR s/n: DRMDZBJPRJPTLYH or Name: m00dify s/n: HUYJHPQJXNYBCRZ Absolute Security Standard V Name: Hazard s/n: ECHVNZQRCYEHHBB or Name: PhatAzz [e!] s/n: RBFXPLUMBPGDFYW Absolute Security Standard V Name: embla of phrozen crew s/n: LTPDTDMAEHNKNTR Absolute Security Standard V Name: FiReAnGeL [EVD] s/n: WTRPBPUCJDMHUHU Absolute Security Standard V Name: CROSSFIRE ROCKER s/n: CYZANWUZUDDEYPU Absolute Security Standard V Name: NSA_CRACKERZ_TEAM s/n: MBGJUGHTYRBPBXR Absolute Security v Name: JUANDA s/n: AFQTGBZPNLERURU Absolute Security V Name: JUANDA s/n: AFQTGBZPNLERURU Absolute Security V Name: ls-Warp s/n: LYLAYLYYJLEBHUC Absolute Security V Name: Evil Ernie 2K [SCB] s/n: GMKKRAPZBJRRXQP Absolute Slots v s/n: Absolute Spades v s/n: Absolute Spades v s/n: Absolute Time Corrector V To install the Key, launch Absolute Time Corrector, click on Register ATC button, copy the key. =begin=0ByWUEFsfRlNqh9H7Pf5D/ C9bwvXWgjyv+VwnuxGt+1VA7VKjZIHgRn3lrtXbSSvIf1nNZfk wwQFlumTn/Lfs6JyepmiEqBAX3FjQpTdHTFYYKhXugsZ2tOEcSr/jqvQnCvc76szUjxT2xw0zxl5/z7dWv+TsonCBQUaSycDCaT4==end= Absolute Time Corrector V To install the Key, launch Absolute Time Corrector, click on Register ATC button, copy the key. tGDTrv3jdpuFc9bCquCRUpLWYfGQ9pR+yGeDP8FqZ4nu VPR29UPEBc OmmjL2luR3ELcoG2fyiaEt6JjGWQcklDnVZaqY9qQ5evApwhRd /F6Jli2/NK oB/ 4s+kMy3R8pPrg5OpGss3eLCnjx+uGGq35ydwtHGv9UDrBnbTA= AbsoluteFTP v Beta 2 Name: xOANON Company: [UCF97] s/n: Expiration: Key: AbsoluteFTP v beta 6 Name: CORE/JES Company: CORE s/n: Exp : never Key: AbsoluteFTP v Beta 7 Name: CORE/JES Company: CORE s/n: Expiration: never Key: AbsoluteFTP v Final Name: CORE/JES Company: CORE s/n: Exp : Never Key: AbsoluteFTP v RC 11 Name: _RudeBoy_ Company: Phrozen Crew s/n: Exp : Never Key: AbsoluteFTP vb3 : Name: RePulsive Company: Pirates Gone Crazy s/n: Exp : Never Key: AbsoluteFTP V Beta 3 Company: CZY s/n: Exp: Never Key: AbsoluteFTP V Name/Company: CZY s/n: Exp: Never Key: AbsoluteFTP V Beta 1 Name/Company: CZY s/n: Exp: Never Key: AbsoluteFTP V Name/Company: CZY s/n: Exp: Never Key: AbsoluteFTP V Name/Company: CZY s/n: Exp: Never Key: AbsoluteFTP V Name: tE Company: TMG Date: s/n: Code: CFBB23BEA69AF33A99 AbsoluteFTP V Name: Barbara Page Company: E.E. s/n: Key: Date: Never AbsoluteFTP V Name: Lonnie S. Porter Company: s/n: LicenseKey: Expiration: Never AbsoluteFTP V Name:CZY Company:CZY Serial Date:Never Key AbsoluteFTP V Name: CZY Company: CZY s/n: Key: Date: Never Absolutely Online v build 17 Name: SiLicon Surfer [PC] s/n: or Name: n03l s/n: Absolutely Online v Name: Delphic s/n: Absolutely Online v Name: DORIS MOREAU s/n: Absolutely Online v Name: coSmoS [True] s/n: Absolutely Online vb37 Name: dustie of blizzard s/n: Absolutely Online V Name: sudiweb s/n: Absolutely Online V Name: dustie of blizzard s/n: Absolutely Online V Name: Walhalla [oDDiTy] s/n: or Name: Shaligar^Lash s/n: Absolutely Online V Name: sudi s/n: Absolutely On-line V Build 42 Name: Registered User Code: Absolutely Online V Name: GARFiELD [rA] s/n: Absolutely Smart Server3 v s/n: Key: yHExiBAiDFzUY Absolutely Smart Server3 v s/n: Key: yHExiBAiDFzUY Absoluter Fast Taskbar v Name: xasx/tnt s/n: nxpwvy Absolutey Online v Name: ls-Warp98 s/n: Abstract Web Studio V Name: ReanimatoR^LasH Password: LasH CrackinG Code: 1AF8-FF7EACD Abuser vb Name: me s/n: Abuser V Name: Byte Ripper s/n: or Name: PC96 s/n: or Name: Phrozen Crew s/n: ABView V Name: Scott Bainbridge s/n: cffjVmecWOOSUYTfT6Yei54Zem Key: XlVlYQPglhVUlmkmPWSQlPTY4f Academia V s/n: AcadLight v97 Key: EUB7 s/n: Acars Loganalyser V Name: LUCiD IS BACK s/n: Accel SpeedTec V Name: JiOO s/n: ACCEL Tech P-CAD S/N AccelDocs v s/n: AD Accelerated CD v Name: shuttle avalon s/n: 1 AcceleratedX v s/n: AcceleratedX v Name/Company: (Anything) s/n: DS0LID Accelerator s/n: ACP4U or s/n: ACP4U or s/n: ACP4U AccelPad V s/n: C1 Accent Composer v Name: DarkBug[Weapon] s/n: CBA23A0BDFAB82 Accent Express s/n: or s/n: Accent Professional v : s/n: or s/n: Accent s/n: Accent v Final Beta : s/n: Access ADI s/n: Access Administrator V s/n: Access Administrator V s/n: Access Animation V Name: Sempai^LasH s/n: WSCWSC Access Animation V Name: TEAM LAXiTY s/n: S50 or Name: Mackoi s/n: WSCWSC Access Animation V Name: crash s/n: W-#### Access Animation V Name: The Netmech^LasH s/n: 5WW#W Access Code Analyzer V s/n: 4C5CB Access Denied v Name: [NUT] s/n: F1EF90ab19EEE4 or Name: James Frazier s/n: Access Denied V Name: James Frazier s/n: Access Denied V Name: James Frazier s/n: Access Denied V Name: James Frazier s/n: Access Denied V Name: Michael Rizzuto s/n: Access Diver v Name: James Company: Shopdown s/n: KqIqKjLkXgHcSvBZQK0TQQMEGIQNIOI Access Image V Name: Sempai^LasH s/n: #C Access Image V Name: TEAM LAXiTY s/n: Access Image V Name: Mackoi s/n: ACIMG or Name: The Netmech^LasH s/n: 3CC#C Access Lock V s/n: Access Manager V s/n: iTN05SE Access Password Recovery V Name: Skboca s/n: 8LU7ZP Access PC s/n: Access Photo V s/n: SHVAL Access Photo V s/n: SHVAL Access to ASP V Name: TEAM REAL! s/n: or Name: TEAM DISTINCT s/n: Access to Delphi Converter s/n: Access To VB v Name/Company: James Bond s/n: Access To VB v s/n: Access To VB v s/n: Access To VB V Name: EMBRACE Company: EMBRACE s/n: Access Wordpoint v s/n: AccessAble Help Desk Professional Edition V Name: (Anything) Company: (Anything) Password: prideandjoy Accessable Help Desk SE V Password: finesthour Access Image V Name: Mackoi s/n: ACIMG or Name: The Netmech^LasH s/n: 3CC#C Access Lock V s/n: Access Manager V s/n: iTN05SE Access Password Recovery V Name: Skboca s/n: 8LU7ZP Access PC s/n: Access Photo V s/n: SHVAL Access Photo V s/n: SHVAL Access to ASP V Name: TEAM REAL! s/n: or Name: TEAM DISTINCT s/n: Access to Delphi Converter s/n: Access To VB v Name/Company: James Bond s/n: Access To VB v s/n: Access To VB v s/n: Access To VB V Name: EMBRACE Company: EMBRACE s/n: Access Wordpoint v s/n: AccessAble Help Desk Professional Edition V Name: (Anything) Company: (Anything) Password: prideandjoy Accessable Help Desk SE V Password: finesthour AccessAble Help Desk Suite V Password: finesthour AccessNfs Gateway v Name: shuttle Company: avalon s/n: JN AccessRecovery V s/n: AccessToVB v Name/Company: James Bond Code: Account Pro vn Name: Gladys Frey s/n: 5ACCAC3FGD6DAB2 Account Pro v Name: Dan K. Hanson s/n: 5A79AC2GEG4E7B9 Account Pro v Name: Gladys Frey s/n: 5ACCAC3F9FAEE1B Account Pro Vd Name/Company: VDK s/n: 6A59AC9BA Account Pro V Name: naManaX Company: Blizzard s/n: 5AD5ACAA3 Account Pro VF Name: Team DW2k Company: (Anything) s/n: 6A68ACD2FE6F1CF Account Pro Vh Name: FLASH! Company: FLASH! s/n: 5A82AC8DEE Account Pro Vm Name: -2EA3+ [HERiTAGE] Company: HTG s/n: 3AD5AC68EDD5 or Name: FLASH Company: Valfritt s/n: 5A82AC8DE Accountant Inc. Pro s/n: Accounting For Delphi Dec FirstPassword: texas SecondPassword: norwich | |
Admin
المساهمات : 50
تاريخ التسجيل : 14/01/
الموقع : cromwellpsi.com
Accounting for Delphi Sep 99 Password: CANADA Accounting Works (one write plus) s/n: A AccountLogon V Email: Nemesis@tntcom s/n: AA29EAED0CE9 Accounts 95 v Name: Antkiller s/n: Accounts 95 v Name: PaulBar s/n: Accounts and Budget V Name: NORAT s/n: - - - NO AccPac Simply Accounting va s/n: ACcrak3 Password recovery for MSAccess: CCardMDS34 s/n AccuChef v Name: ZiuHu/TEX99 s/n: AccuChef v Name: JudgeD s/n: dlmsppea1 AccuChef v Name: (Anything) s/n: dlmsppea AccuChef vc Name: Licensed User s/n: or Name: RayBieZ s/n: AccuChef vf Name: Raybiez s/n: AccuChef vg Name: LIDONG s/n: AccuChef Vj Name: Raybiez Cracking s/n: AccuChef V Name: Nemesis] s/n: 14ED7F3E56B5A6FE Accum V Name: TUC PC2K s/n: Accum Vd Name: +DzA kRAker s/n: Accurate ID Standard V Name/Company: (Anything) s/n: advancededi42 Accurate ID Standard V Name: MANiACS Company: MANiACS s/n: advancededi53 Accurateburn MP3 Audio CD Maker V Name: KARHU s/n: hLtFmlicSAcAeajN or Name: Shaligar^Lash s/n: CeHHSGOImhSDDYke or Name: Jumpbull [eVC] s/n: HCNVNvpLDGGlVSnV Accurateburn MP3 Audio CD Maker V Name: Nemesis] s/n: iiSGIaYGcNvGiVnj Accurateburn MP3 Audio CD Maker V Name: Mackoi s/n: SVCnpmCVDSCnNYVG Accurateburn MP3 Audio CD Maker V Name: Bush Jr s/n: LRRmhAFVSFYWWpRp or Name: Sempai^LasH s/n: vRejGSaHVCpFFvIS Accurateburn MP3 Audio CD Maker V Name: Neur0n / FLN s/n: nIkWn3FVVaRICiLC AccurateBurn MP3 Audio CD Maker V Name: Neur0n / FLN s/n: nIkWn3FVVaRICiLC AccurateBurn MP3 Audio CD V Name: Chicane [dF] s/n: GsjvlpnFADSfVItj AccurateBurn MP3 CD Maker V Name: GARFiELD [rA] s/n: LGYVlGkGHQGKImAH AccuSet 32 Professional Edition vB Code: CB1E AccuSet vB Name: AAAA-HID98 Company: HiD Present s/n: Accutext v s/n: Accver MS Access Version Checker V s/n: acaB ACDExpress v Name: Nordic Company: - Code: ACDExpress v Name: Nordic Company: - Code: ACDExpress v Name: DSi 4 LIFE Company: DSi TEAM Code: ACDExpress V Name: YoKe Company: tHE cRACKiNG aNSWER s/n: ACD-See Powerpack Suite Retail V s/n: ACDSee PowerPack V s/n: ACDsee SR1 PowerPack Retail S/N ACDSee v Name:Sender s/n ACDSee v+2 name:letis s/n:+tHE riDDLER [uCF] ACDSee v Name:ACDsee Code ACDSee v Name:sender Code ACDsee vb4 Name:Kermu Code ACDSee v+7 name:kermu s/n ACDSee v+7 name:mARQUIS s/n ACDSee v Name:Sender Code ACDSee v Name:ACDsee Code or Name:sender Code ACDSee v Name: kOUGER! s/n: ACDsee v Name:mISTER fANATIC s/n or Name:Sander s/n ACDSee v Name: letis s/n: ACDSee v Name: Han Solo s/n: ACDSee v Name: BaRT SiMPSoN s/n: ACDSee V s/n: or s/n: or s/n: ACDSee V build S/N،G ACDSee V build S/N،G ACDSee v bulid s/n: or s/n: ACDSee V German s/n: or s/n: or s/n: or s/n: or s/n: ACDSee V s/n: ACDSee V SR1 Power Pack S/N،G ACDSee V SR-1 S/N Name ACDSee V Code: Ace Architectural Classic Drafting Pack V s/n: AR-C-W Ace Bible Pro V s/n: aprab Ace Bible V s/n: aprabACE Contacts Manager v : UserKey: U8JMHTG RegKey: 9B98C2DE1F4B7EE Ace Bible V s/n: aprab Ace Clock v Name:team ORiON Emailrion99@cromwellpsi.com Code:ACY1Y0I8T6Z3N3N4 Ace Control V Name: (Anything) s/n: EGHACIS4F6D23 ACE Expert Ftp v Name:Black Thorne - Phrozen Crew Code:SM6TSAB3A-L4YUV Ace Expert v Name: Sn0wman s/n: 8STYHTJ-0ZP-3JZ9D8 Ace Expert with Icons v Win95/NT : Name: Shock'97 s/n: IYE-YJ3-YT7Z6ITZ6 Ace FTP Name: fungus of blizzard s/n: F48RST-V73PVM-AJ8AFN5CT Ace FTP Name: fungus of blizzard s/n: F48RST-V73PVM-AJ8AFN5CT Ace Ftp a Name:The Master DaVinci Code:3B7UL43MVJLAVP-AM85FT ACE FTP V Name: ReanimatoR^LasH s/n: XXP6V3-FUTHLW-QDB4XX-U1QE8U or Name: Sempai^LasH s/n: 22Z9YR-MKQAFV-PZZY2A-W7YRU5 Ace HTML Pro V Name: Softappz2k ID: EWTF-GXZJ-BPLL-QCUG Code: B3VB-4MCN-WPYW-FTJU Ace HTML Pro V Name: tHE EGOiSTE [TMG] s/n: NC5H-AWY4-QDPT-KSQK Ace HTML Pro V Name: TEAM ElilA s/n: YVHI-TCPR-HPCX-DMWZ Ace HTML Pro V Name: Free User s/n: Q4LB-KG9X-Q8PB-3TN6 Ace HTML Pro V Name: Free User s/n: Q4LB-KG9X-Q8PB-3TN6 Ace HTML Pro V Name: Free User s/n: Q4LB-KG9X-Q8PB-3TN6 or Name: Mackoi s/n: R7UG-PNNN-JYUZ-ZZZZ Ace HTML Pro V Name: Free User s/n: Q4LB-KG9X-Q8PB-3TN6 Ace HTML Pro V Name: Free User s/n: Q4LB-KG9X-Q8PB-3TN6 or Name: Nemesis] ID: 9MC6-CRKH-B9N5-XKQF RegCode: NQUU-9AEX-D2CC-QQ9D Ace HTML Pro V Name: Free User s/n: Q4LB-KG9X-Q8PB-3TN6 Ace HTML Pro V Name: MackOi DBC s/n: JQVB-HHAC-ZHFQ-W9XU Ace HTML Pro V Name: TEAM LUCiD s/n: SWQH-ZMSC-GNTH-C9EF or Name: Silver Storm s/n: V5MF-NQHD-KMMU-GFDU Ace HTML Pro V Name: Sponge Uk - TNT[CraCK!TEaM] s/n: FVTW-5YAD-LAFT-HMMQ Ace HTML V Name: TeRMiNaToR [ACF] s/n: FNVG-IBQH-RJSR-HPHI Ace HTML V Name: MbR ID: s/n: WMN9-PKU5-NCGZ-ZZZZ Ace of Humor V Name: Dark Lord / FALLEN s/n: 8U Ace Reader v name: davy - blizzard License: 1 s/n: 5sZY6Pu65I Ace Reader Vc Name: Jumpbull [eVC] Copies: 20 s/n: 4wBnJaZ73n Ace Replace Name: wizard-x [pdn] s/n: Ace ScreenSaver V s/n: RUxaUwYM Ace V Name: Ak s/n: ACERYHFJQIUYI8SGWKPEVZ0BID3 AceCapture V Name: eax^CrackPL s/n: AceCapture V Name: eax^CrackPL s/n: or Name: The Netmech^LasH/EaGLE s/n: AceExpert v Name: Sn0wman s/n: 8STYHTJ-0ZP-3JZ9D8 AceExpert v HTML Editor Name: jog [DNG] s/n: YJH7PZUJ8Z-EV1UAEV82A AceExpert va Name: SiraX/[DNG98] s/n: 82Z5IX2-ZVEI1BERZ AceExpert vh Name: Republic s/n: BPQU-YXEV-E85S-F2MR AceExpert v Name: Registered User s/n: XLYA-6DDB-1AMJ-2TXS AceExpert va Name: ProfViper s/n: IWPV-XJFW-IDK4-P5VS AceExpert vb Name: Predator/[FAITH] s/n: YALCGC-CFGN-C2QX AceExpert vc Name: Sickie [TbC] s/n: EN5Q-SYQ3-MTV8-EJZP AceExpert vd Name: Name: -/--Predator/FAITH/- s/n: BQSC-IZZS-DQP1-ASYL AceExpert vf Name: CoKeBoTtLe99 s/n: MTA4-WNPK-SMJL-YWPR AceExpert vg Name: DEFAULT s/n: 7Q8X-1CXQ-B9SZ-ZZZZ or Name: IND s/n: FNAJ-T5GZCZ-ZZZZ or Name: __RayBieZ__ Code: AIJP-KD8V-IKUF-SEY4 AceExpert vh Name: HTTP://CHZHYCOM s/n: Code: 1UQU-L1Q4-KJGF-1YEY or Name: RbZ_cRacKiNG s/n: (Blank) Code: XSVH-LVNI-Z9GC-EPQD AceExpert vf Name: Fluke s/n: NPGI-UDLH-JMWZ-ZZZZ AceExpert vg Name: EinZtein of Blizzard Code: s/n: BQGP-7PQI-E1TH-NRPP AceExpert with Icons v : Name: Shock'97 s/n: IYE-YJ3-YT7Z6ITZ6 AceExpertVi Name: LoST/MFD s/n: YHLN-J2YH-2VUY-AN5E or Name: C0Ke s/n: E8VN-2Z3Q-PWZC-LHN1 or Name: +s0nYK s/n: ESDJ-UWNK-N9AZ-ZZZZ AceFTP vb Name: jog [DNG] s/n: 74FEV2-NB8RUS5C4-V7A5FT AceFTP v Name: fungus of blizzard s/n: F48RST-V73PVM-AJ8AFN5CT AceFTP v Name: Edge-` [Fallen 98] s/n: NLJ-CE7MYR-VT AceFTP v Name: Arfa [PCY] s/n: SAP-AA34NJ-FBSMLYEA4 AceFTP v Name: CoKeBoTtLe99 s/n: 64SE7BEYT-SRL5N5-F7AU3E AceFTP va Name: -/--Predator/FAITH/- s/n: 4BM-CY7LU6B-AR3EF2 AceFTP vb Name: CoKeBoTtLe99 s/n: 64SE7BEYT-SRL5N5-F7AU3E or Name: RbZ_cRacKiNG s/n: YALCR64YT3UV7C4 AceFTP V Name: LoST/MFD s/n: LAANJFB-SMLYEA46P or Name: CZY s/n: JLA-VPAMFT74N7-LE AceFTP Va Name: CZY s/n: JLA-VPAMFT74N7-LE AceFTP V Name: CZY s/n: JLA-VPAMFT74N7-LE AceFTP V Name: notice! [DBC] s/n: 25C5F7-A23BF4-VENUR AceFTP V Name: CZY s/n: JLA-VPAMFT74N7-LE or Name: Code'LasH s/n: 64L5VMC53TS7YJ-YA6P2M AceFTP V beta 3 Name: iNCREDiBLE FiGHTER s/n: 7BXN-NZT3-BBFC-AUFE AceFTP V beta 8 Name: cromwellpsi.com [AmoK] s/n: YMCK7B-HMV6QSRMKP AceFTP V Name: Free User s/n: AUXZ7PK-TTMDZC-WMBHAU or Name: DiSTiNCT s/n: BM29PK-HB7WATHL4A-DQU6CN AceFTP V Name: Free User s/n: AUXZ7PK-TTMDZC-WMBHAU or Name: Nitrus s/n: 7WUAZFF8-V31HNSTPY AceFTP V Name: Free User s/n: AUXZ7PK-TTMDZC-WMBHAU AceFTP V Pro Name: DiSTiNCT s/n: BM29PK-HB7WATHL4A-DQU6CN or Name: Free User s/n: AUXZ7PK-TTMDZC-WMBHAU AceHTML Poo V Name : Arcane / Phrozencrew s/n: DXYB-VCRB-TRGU-PHVU AceHTML Pro V Name:Free User Code:Q4LB-KG9X-Q8PB-3TN6 AceHTML Pro V Name:Free User Code:Q4LB-KG9X-Q8PB-3TN6 AceHTML Pro V Name:Free User Code:Q4LB-KG9X-Q8PB-3TN6 AceHTML Pro V Name:Free User Code:Q4LB-KG9X-Q8PB-3TN6 AceHTML Pro V Name : Arcane / Phrozencrew s/n: DXYB-VCRB-TRGU-PHVU AceHTML Pro V Name: Sponge Uk - TNT[CraCK!TEaM] s/n: FVTW-5YAD-LAFT-HMMQ AceHTML Pro V Name: Sponge Uk - TNT[CraCK!TEaM] s/n: FVTW-5YAD-LAFT-HMMQ AceHTML Pro V Name: DiSTiNCT s/n: A5FP-DTGA-ZRQF-HWXS AceMacro Pro V Name: (Anything) s/n: AceNotes v Name: SiraX [CORE] s/n: AceNotes v Name: SavaGe [PC] s/n: AceNotes va Name: independent s/n: AceNotes vb Name: Orion s/n: AceNotes vc Name: Orion s/n: AceReader Pro Deluxe Vb Name: TEAM ElilA Licences: site license s/n: NbPBAmi2yU AceReader v Name: warez License : 1 s/n: 4sVE6Wo87H AceReader v Name: Versus Licenses: 99 s/n: 1wVS1Ho07G AceReader v Name: Gorgeous Ladies Of Warez s/n: 3rHnJeY74n Licenses : 1 AceReader v Name: webmasta[DC] s/n: 3sHnKiX57n or Name: Raybiez Cracking Licenses: 99 s/n: 5xEmKhS27n AceReader Vd Name: Raybiez Cracking Copies: 99 s/n: 5xEmKhS27n AceReader V Name: +s0nYK [iNTENSiTY] Licenses: 99 s/n: tD4Ka4n5mR Aces of the Deep s/n: | |
What’s New in the 602 Messaging Server v3.32c serial key or number?
Screen Shot
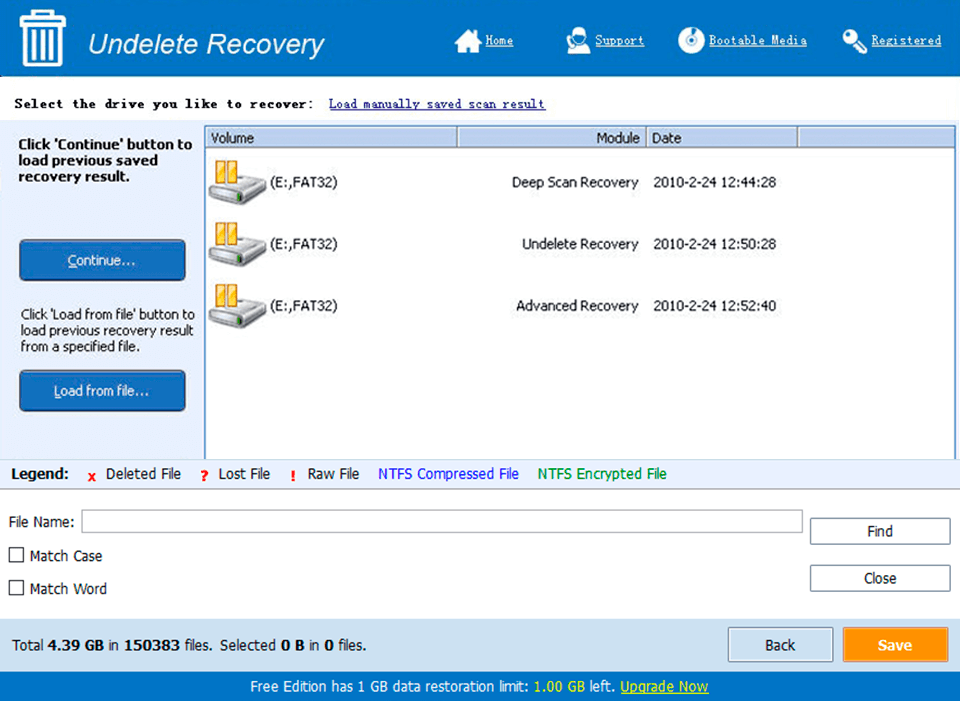
System Requirements for 602 Messaging Server v3.32c serial key or number
- First, download the 602 Messaging Server v3.32c serial key or number
-
You can download its setup from given links:


